Password Strength Checkers - Mostly Useless...
Think your password is strong? Ever trusted a password strength tool online (or maybe you don't trust anything)? You might be surprised to see how far off the mark some of the most popular password strength tools are.
As security practitioners and organisations promoting or advising on cybersecurity, we should strive to ensure we provide guidance that is accurate.
This is even more important for guidance that will be provided to the general public in situations where there's no opportunity to provide additional context.
With that expectation in mind, imagine my shock discovering that 4 out of the top 10 search results for password strength tools offered very questionable password security advice.
Google Has the Answer
Over and over again, the simplest things like poor password use show up as findings in penetration test reports.
Digging deeper, the root cause is often one of the following:
- People are complacent.
"Oh but it won't happen to me, I'm not that important." - Jane Doe
I even know quite a few cyber security practitioners who have poor password hygiene. You know who you are if you're reading this, you know better! - People don't know better.
Better password education! I can help with this!
But for a second let's pretend I'm a budding security enthusiast who wants to learn about how to craft better passwords. Put in those shoes, I think searching for password strength tools would be a route I might consider.
Let's take a look at security.org's password strength tool.
Their website looks pretty polished and on the surface it seems like they'd be able to give some good advice. I even see some big logos I recognise!
Using 'Ministry2023!' as an example password, conventional wisdom might have you believe this is a pretty decent password. It's relatively long at 13 characters, uses upper case characters, digits and even a special character.
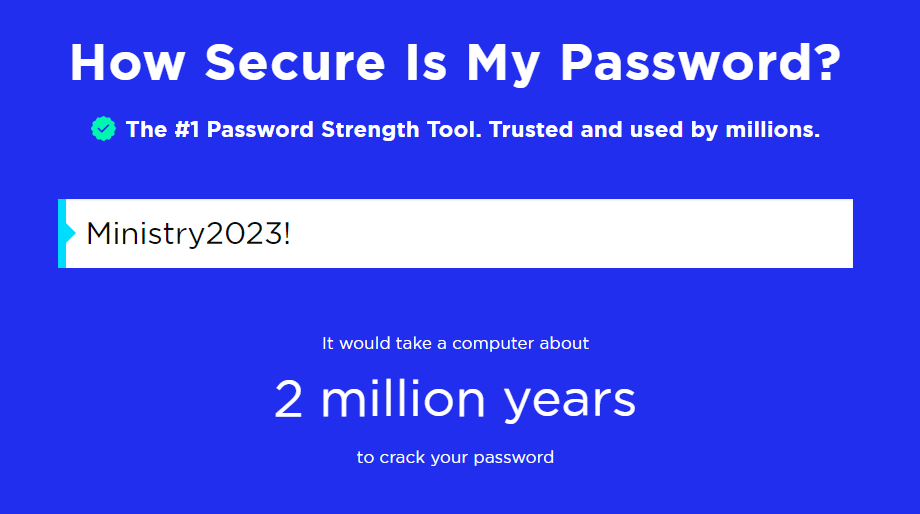
security.org's password strength tool would agree that it's a strong password estimating that it would take 2 million years to crack this password!
Some of the other top tools agree with this evaluation.
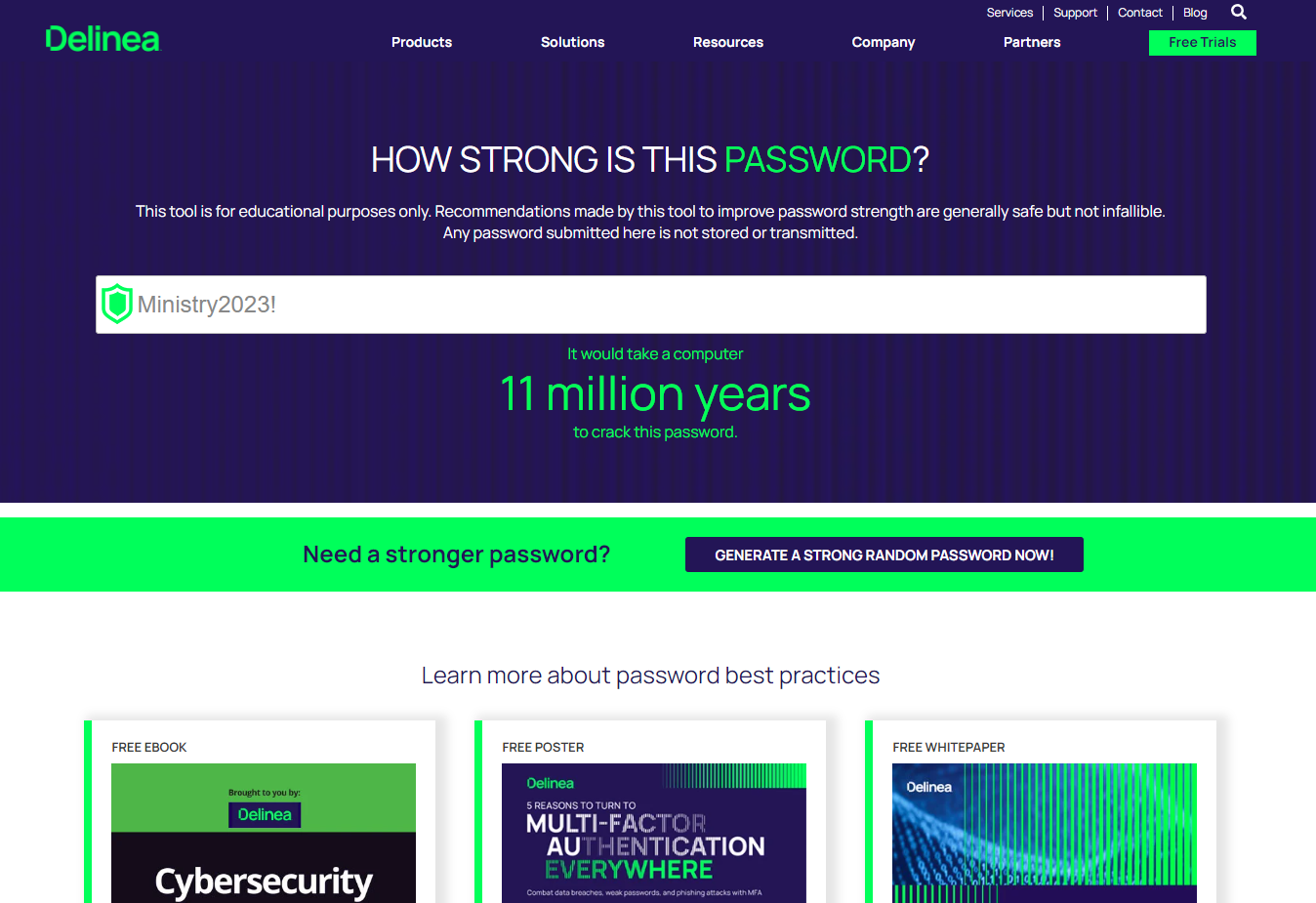
11 million years!
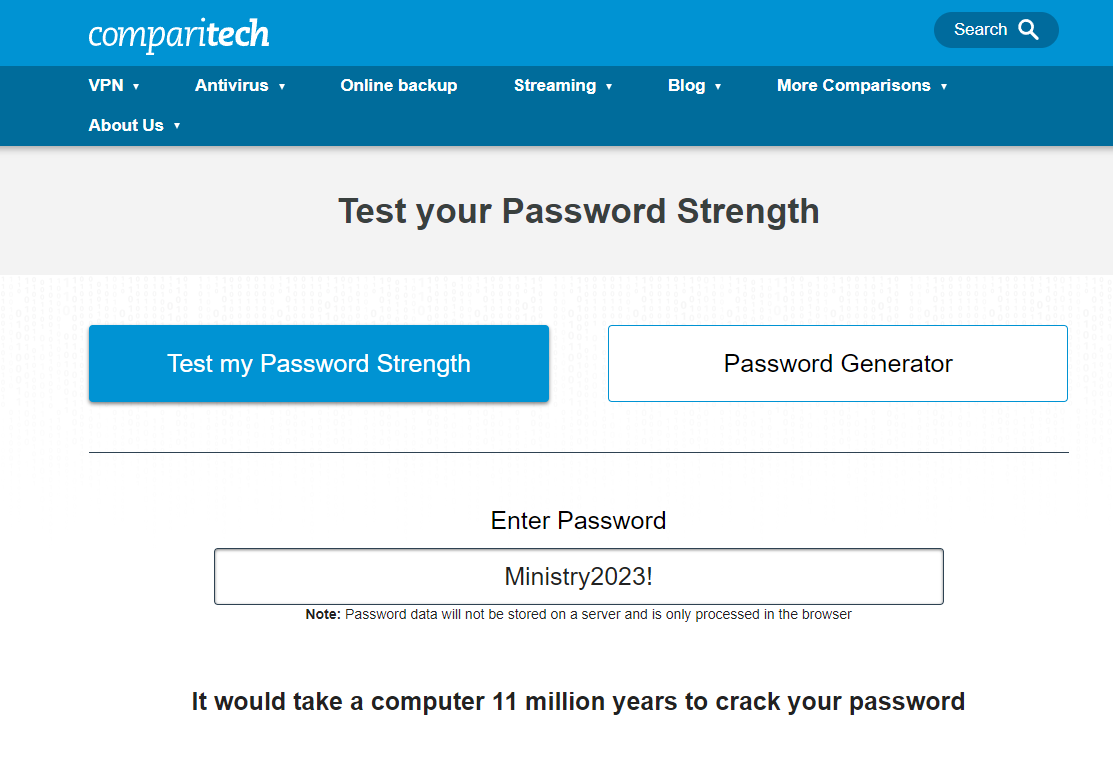
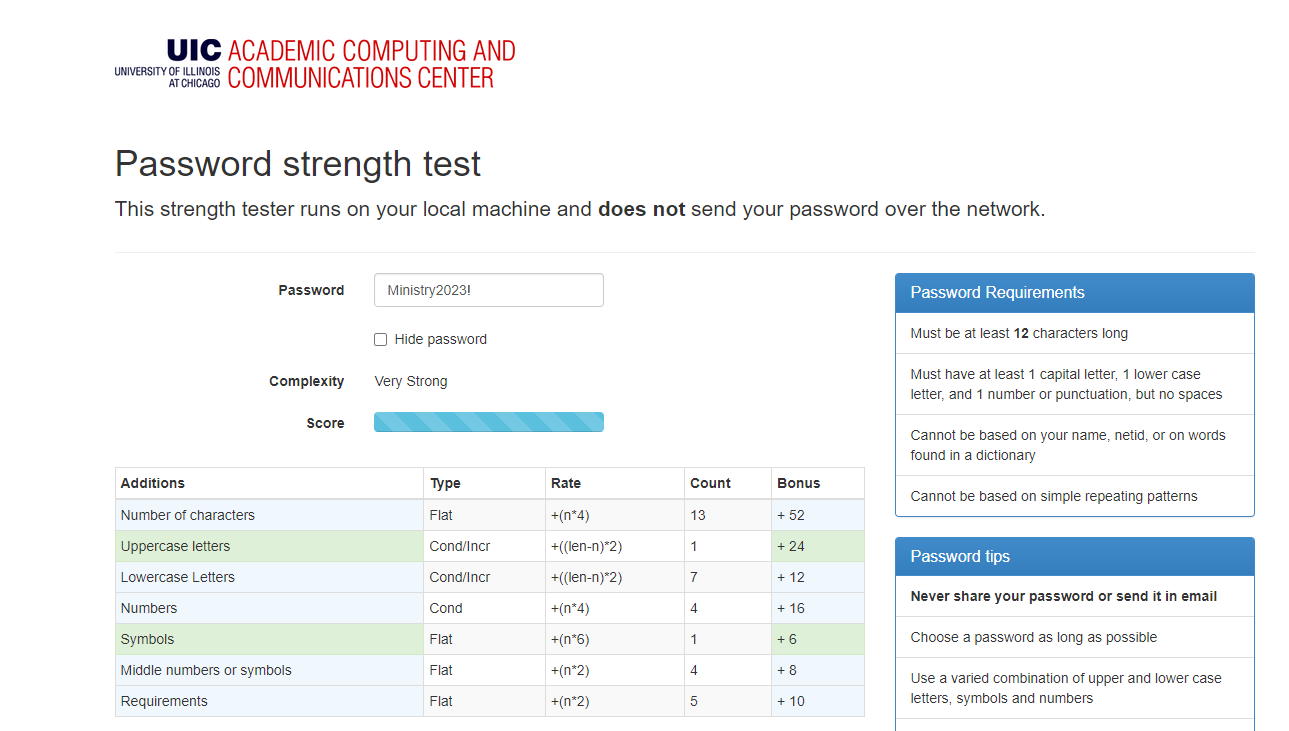
The Reality
Unfortunately the reality is a bit different to what the highlighted tools are suggesting.
Using a single $650 graphics card (a RTX 3070), our password in the Windows hash format (NTLM) took just 8 SECONDS to crack.
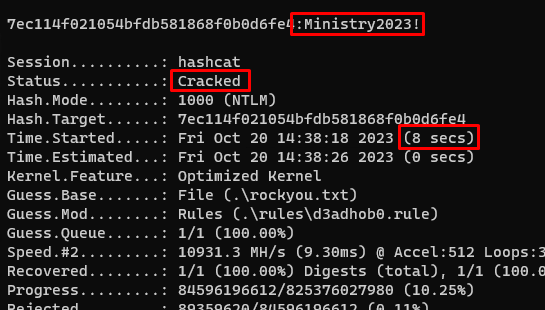
That's quite a bit shorter than 2-11 million years.
To understand why these tools are so far off, we need to go into a few details.
Some Technical Information
When we're talking about cracking passwords, there are two main groupings of attacks:
- Online attacks - this is where an attacker is trying to login as you would to online systems. They may be slowed down by controls such as account lockouts where multiple failed attempts will stop them in their tracks.
Attackers performing online attacks are looking at hundreds to possibly thousands of attempts an hour. - Offline attacks - this is where an attacker has obtained a representation of your password (the hash) but not your actual password; a breach in a third party service you use is probably the most common way attackers may obtain your password hash, if you reuse that password and don't change it before attackers get to those accounts you have a problem (there are also other methods which are out of scope for this blog).
Attackers performing offline attacks are only limited by the speed of their hardware at their disposal, we are now talking about millions or even billions of attempts a second.
While our chosen password might withstand an online attack, where possible we should choose passwords that are resilient against the worst-case scenarios: offline attacks. Based on some of the estimates from these tools, they seem to be preparing users providing estimates relevant to offline attacks as well.
Why are these tools so far off the mark? The answer seems to be that they are taking a relatively simplistic approach to performing these offline cracking estimations.
A naive approach to estimating password strength would count the number of characters in your password and then calculate the time a modern computer would need to cycle through every possible permutation.

While the naive approach is theoretically accurate, humans don't typically pick completely random passwords (e.g. "eGng/eh5.Vdz").
- Humans like to pick words for passwords.
ministry - If we are forced to add an upper case character, we like to capatilise the first letter.
Ministry - If we are forced to add some numbers, we like adding them at the end of our password or instead substitute characters in predictable locations (e.g. zeroes for 'o's).
Ministry2023 - Finally if we are forced to add a special character, we once again like adding them to the end of our password.
Ministry2023!
Modern password cracking tools and techniques exploit these human behavioral patterns. They use large wordlists containing dictionary words and 'rules' to adjust each word in the wordlist with variations like those I described earlier.
Not all 13-character passwords are of equal strength.
My Recommendation
Here's what you should do when it comes to making strong passwords.
- Use MFA everywhere you can - I know it's not technically a password tip.
- Don't reuse passwords.
- Use a password manager to help with this - I use Bitwarden (unaffiliated).
- If your password is randomly generated, 12 characters is fine.
- If you really just want to use one word, at least don't be predictable.
- e.g. Using the same characters from our bad password whilst being less predicatable Ministry2023! -> mINIs!20try23 - common hashcat rules are less likely to have coverage for this.
- Use multiple words, password length is by far the most important attribute with some digits/special characters to meet validator requirements.
Contacting the Tool Maintainers
The organisations that maintain these tools might not be aware of modern password cracking techniques so I contacted them so they could make any necessary changes.
- security.org - email sent 20/09/23
- delinea.com - email sent 13/10/23
- comparitech.com - email sent 13/10/23
- uic.edu - email sent 13/10/23
Unfortunately, none of them have responded thus far.
Some Closing Thoughts
- Tools that provide advice like this can do quite a lot of damage to the cause of closing the knowledge gap between cybersecurity practitioners and end users on crucial topics like passwords. I do hope that these tool maintainers act on improving their tools or include more context to help educate their users.
- The responsibility of closing this knowledge gap shouldn't rest solely on the shoulders of those in I.T. or Cybersecurity. It's not always practical to tell the only system administrator in a company to squeeze in time for staff education amidst their myriad of other duties. End users must also step up, taking the initiative to educate themselves on these vital subjects. Everyone has a role to play.
- Would instating a regulatory framework for cybersecurity advice help reduce the amount of cyber misinformation, much like financial advice in Australia? I guess on reflection that's not working very well either.

