Disclosing a Tic Tac Bow Vulnerability to Project 99
eSports were included this year for the Olympics, which got me thinking: can you hack your way into the Olympics? This blog shares a short story of discovering and disclosing a vulnerability to Tic Tac Bow developer, Project 99.
Cheating in eSports has been around for a while. The tug-of-war between cheaters and game developers creating anti-cheat tooling is reminiscent of the ongoing duel between malware devlopers and endpoint anti-virus developers. It's a digital arms race.
Traditional sports typically have uniform regulations and enforcement methods. However, when we talk about eSports, the picture varies widely. How easy it may be to cheat in a game may be largely dependent on the maturity of an individual organisation's application security practices and investment into anti-cheat mechanisms.
Therefore, when the IOC announced its plan to launch an eSports series in 2023, it piqued my interest. It made me ponder a wild possibility: Could someone hack their way into the Olympics and at least qualify?
The initially confirmed featured games across nine sports are:
* Archery (World Archery Federation, Tic Tac Bow),
* Baseball (World Baseball Softball Confederation, WBSC eBASEBALL™: POWER PROS),
* Chess (International Chess Federation, Chess.com),
* Cycling (UCI, Zwift),
* Dance (World DanceSport Federation, JustDance)
* Motor sport (Fédération Internationale de l’Automobile, Gran Turismo).
* Sailing (World Sailing, Virtual Regatta),
* Taekwondo (World Taekwondo, Virtual Taekwondo)
* Tennis (International Tennis Federation, Tennis Clash)
Upon first glance at the list of games selected for the tournament, I was struck by the blend of popular games from well-established publishers alongside lesser-known titles like Project 99's Tic Tac Bow.
The importance of this mix should become apparent when we consider cyber security. Smaller companies often have less financial resources to invest in robust security measures or dedicated security staff. Given the worldwide attention that the Olympics naturally garner, unprepared smaller publishers could potentially face significant problems.
With that in mind, I decided to take a quick look.
Taking a Peek
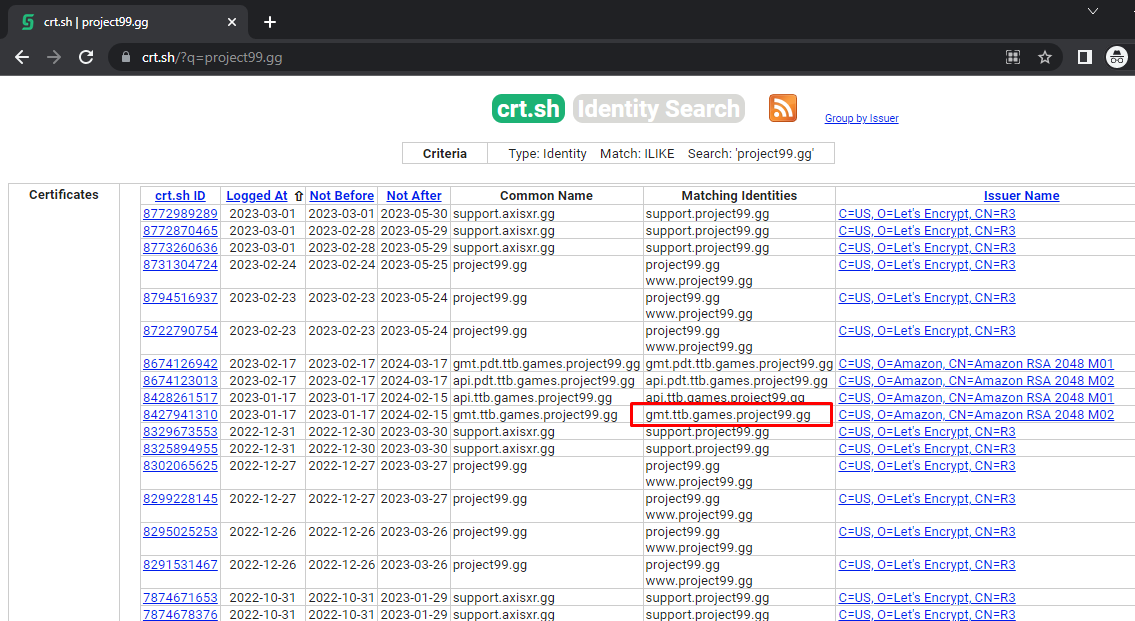
When I'm beginning an investigation into a company's attack surface and all I have is a domain, I often turn to https://crt.sh/. While not strictly a cyber security tool, it uses certificate transparency information, which can be incredibly handy for discovering subdomains.
A quick search using this tool usually reveals several newly created certificates. Among them, highlighted is as subdomain which will be the focus of interest for this blog.
Upon visiting the given URL, I'm met with a login page and an ominous warning about unauthorized access potentially leading to legal consequences.
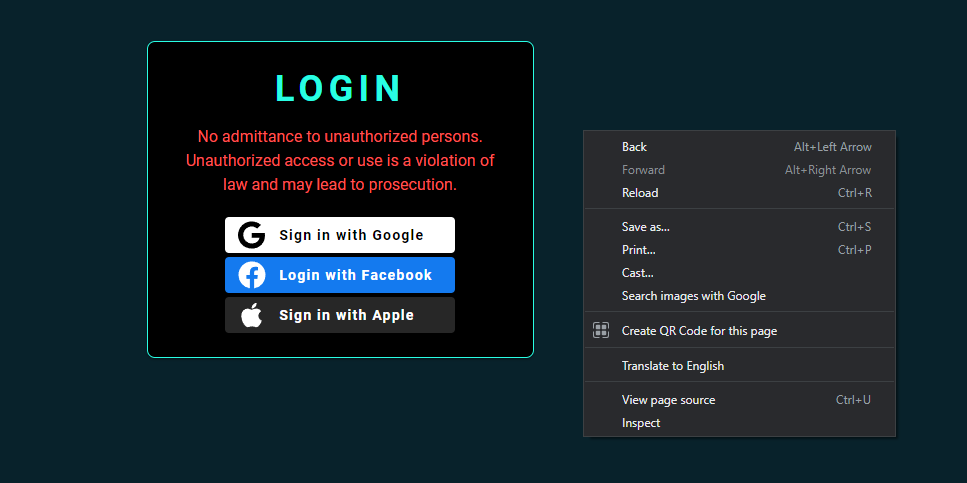
Not wanting to push the threshold too far, we can at least confirm whether their metaphorical front door is locked/their authentication mechanism is functioning properly.
Using the 'Inspect Element' tool, the JavaScript embedded within websites can often reveal references to certain URL paths, most of which should only be accessible after successfully authenticating.
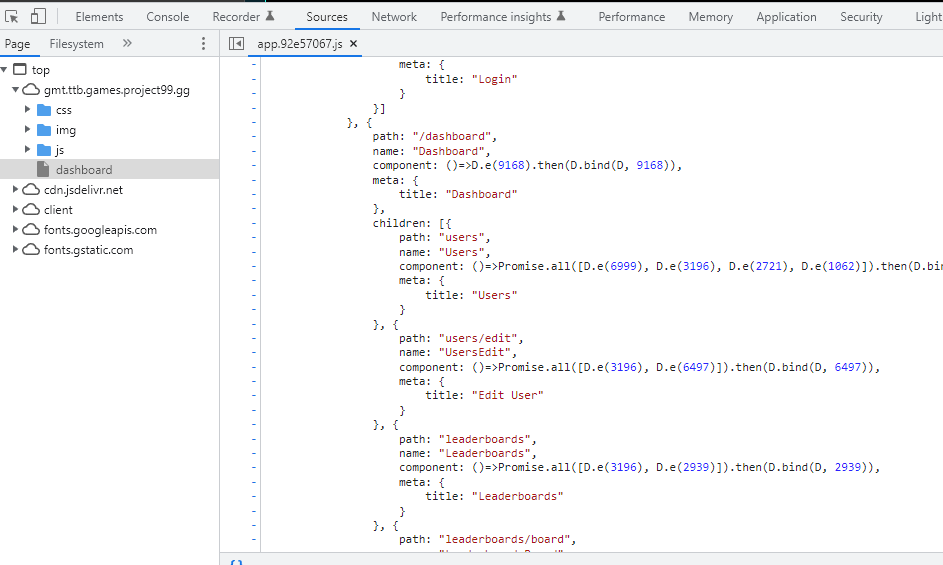
Ideally, without proper authentication, attempts to access these paths should yield an unauthorized response and no content.
Surprisingly though, it seems that the authentication checks for the relevant backend API endpoints was either not working as intended or had been disabled. The login page in this case reminded me of this gag from the Simpsons.

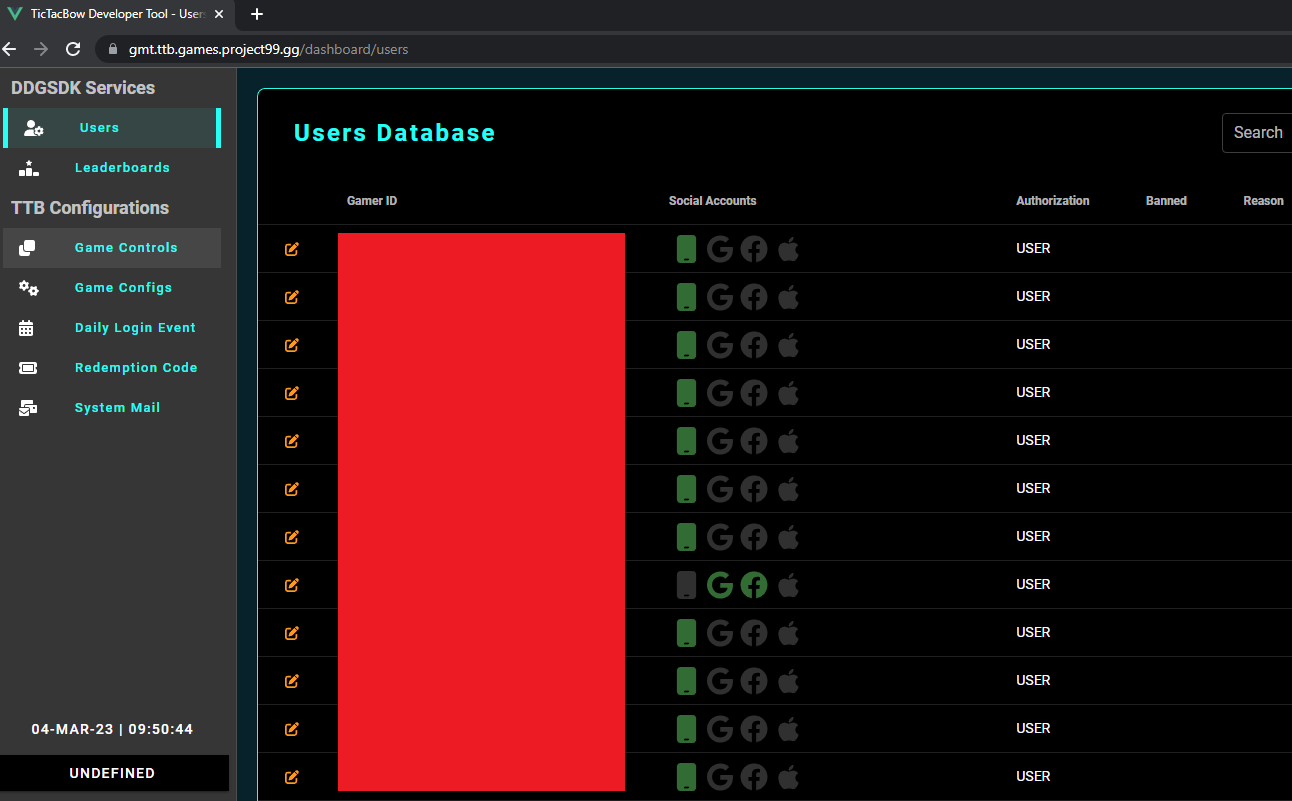
Simply adding /dashboard to the end of my URL bar was enough to get past the login page.
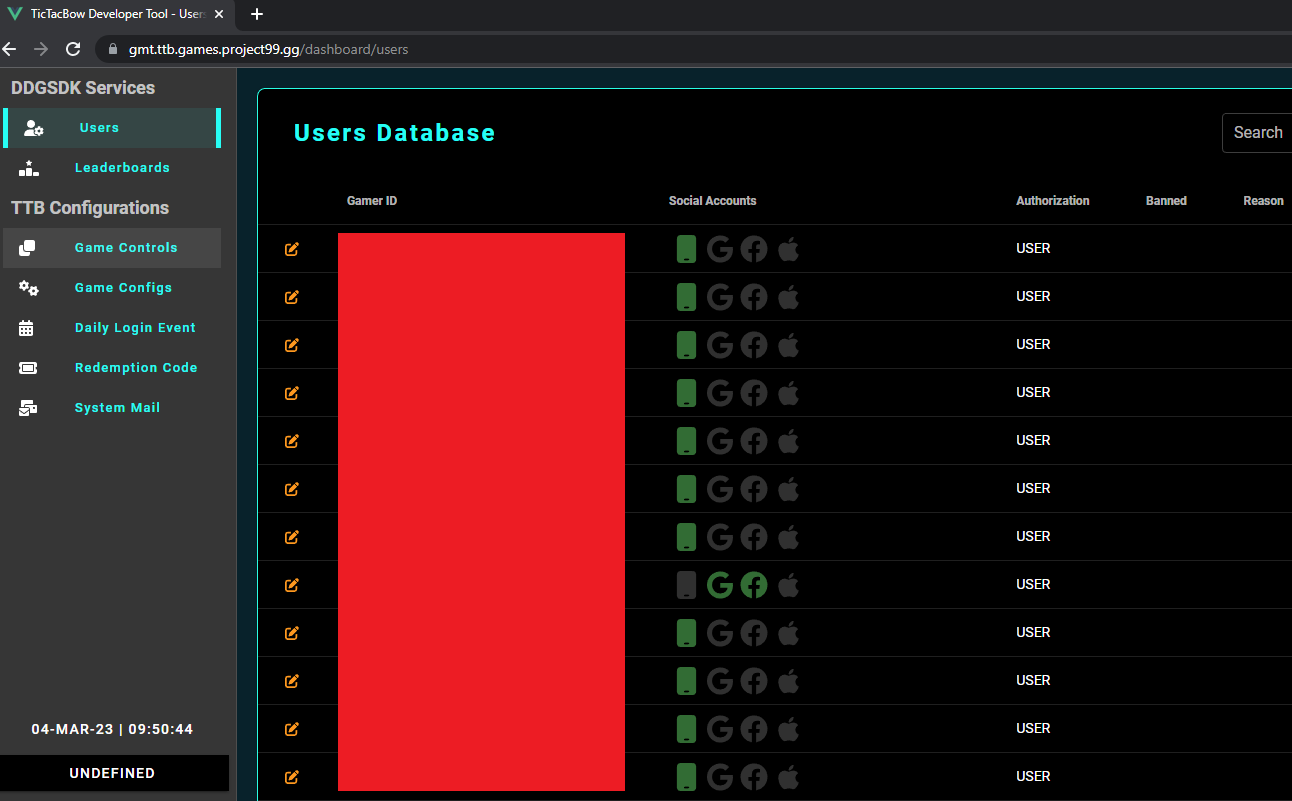
The dashboard appears to be an administrative tool for Tic Tac Bow used to administer users, modify leader-boards and configure settings for the game.
It's now time to craft a disclosure email to alert them about their broken authentication. Identifying an appropriate contact within the organization proved to be a bit challenging, but after some digging, I was able to locate a cybersecurity-related email address within the company's privacy policy.
Fortunately for Project 99, the issue ended up being relatively inconsequential. They responded quickly and confirmed that:
- The issue was valid.
- They clarified that the problem affected a 'test' environment and it did not contain production or sensitive data.
- They had located and rectified any other instances of a similar nature.
- They expressed their gratitude for my disclosure.
Takeaways
My hopes of capturing Olympic Gold will have to stay as mere dreams for now. However, on a positive note, there's some takeaways from this experience:
- A01:2021 – Broken Access Control is the number 1 spot in the OWASP top 10 and with good reason, it is by far over and over again the most common vulnerability class I encounter.
- Never take it for granted that your vulnerabilities will go unnoticed. If a cursory 5 minute look can uncover issues, think of what a determined malicious attacker could do with ample time. Psst reach out for a penetration test or appsec program maturity assessment if you're now thinking about your own attack surface!
- Publish a security.txt file to help people report vulnerabilities to you.
- It's a given that every organization will face cyber security challenges. What matters more, perhaps, is how they respond to these issues when they surface. On this front, Project 99 did well here wrt. response times.
Disclosure Timeline
- March 4 2023: Vulnerability found.
- March 4 2023: Email drafted and sent to [email protected].
- March 6 2023: Email received confirming the issue affected a test environment with no production data and that the affected instances had been identified and addressed.
- March 11 2023: Blog post sent to Project 99/Refract for review prior to publishing.
- March 30 2023: Project 99 management felt that the blog post was factual and objective however requested the blog be published after Olympic eSports week. I honored their request.
- June 22-25 2023: Olympic eSports week.
- June 27 2023: Email sent to Project 99 requesting confirmation to proceed with publishing blog, no response received.
- July 10 2023: Follow up email sent, no response received.
- August 2 2023: Blog published.

