ST4S Assessment
So you’ve just been told you need to meet ST4S requirements? Broken down into parts the ST4S framework is relatively straightforward.
If you’re working with schools or education departments, understanding what’s involved to meet the ST4S assessment framework can be daunting - especially if you don't have much experience dealing with cybersecurity.
Safer Technologies 4 Schools (ST4S) has been developed to enhance the security, privacy, interoperability and online safety of software applications and services commonly used by Australian and New Zealand schools.
Fortunately the framework actually sets out clear expectations for the controls you need to maintain. Like most things in security, it becomes manageable once you break it down into parts.
This post focuses on two areas in the ST4S assessment:
- Penetration Testing - what's actually required and how to approach it.
- Organisational Policies - what is a policy and what do you need to maintain to align with the framework's expectations.
What are the Penetration Testing Requirements for ST4S?
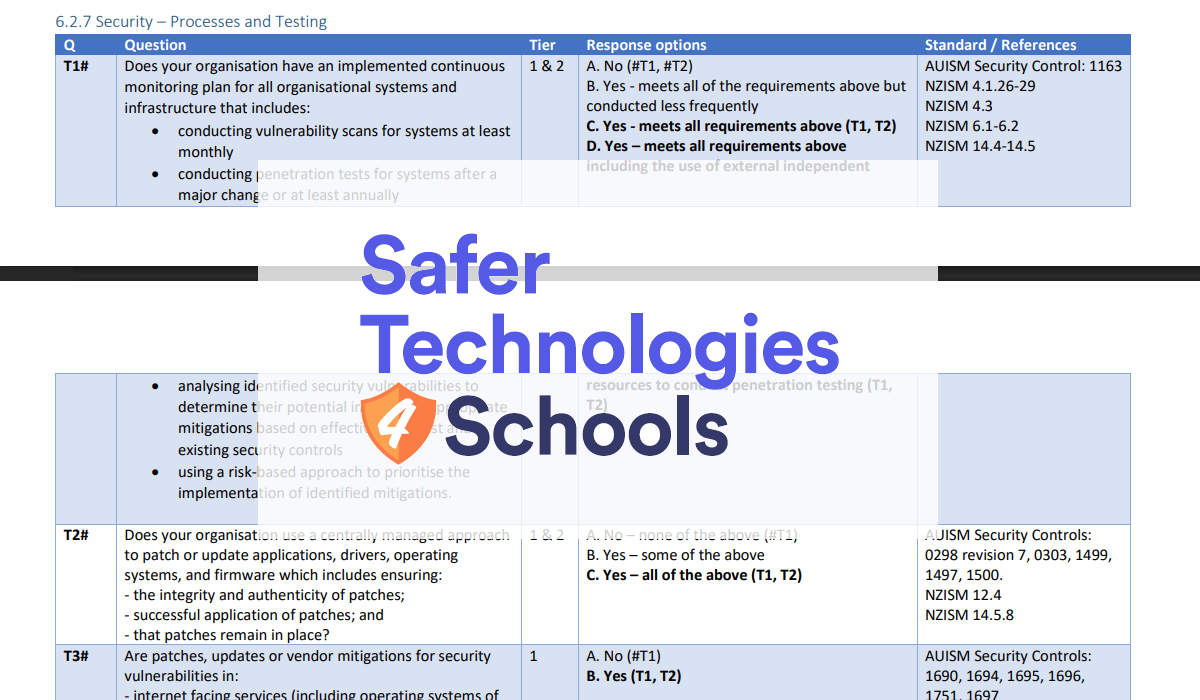
The main control in ST4S is 6.2.7 - T1.
6.2.7 - T1#: Does your organisation have an implemented continuous monitoring plan for all organisational systems and infrastructure that includes:
* conducting vulnerability scans for systems at least monthly
* conducting penetration tests for systems after a major change or at least annually
* analysing identified security vulnerabilities to determine their potential impact and appropriate mitigations based on effectiveness, cost and existing security controls
* using a risk-based approach to prioritise the implementation of identified mitigations.
What's the difference between Vulnerability Scanning and Penetration Testing?
Although vulnerability scanning and penetration testing both aim to identify weaknesses in your systems, they’re quite different in scope, purpose, and depth.
Vulnerability scanning is 100% automated and, for the most part, can only find surface-level vulnerabilities. The benefit of automation however is that it can be run frequently making it ideal for catching low-hanging fruit.
By contrast penetration testing is largely manual (AI is not quite there yet in 2025). Skilled testers analyse the application’s context, user interactions, and system behaviour to uncover vulnerabilities that automated tools would miss.
What is a 'major change'?
This typically means changes that impact security controls, or introduce significant new features that might raise your risk exposure. Here are some examples:
- Introducing a new authentication method, such as SSO or MFA integration.
- Adding a new identity verification feature that asks users such as teachers or parents to upload passport details or other forms of ID.
- Replacing authentication and authorisation logic to introduce new RBAC features.
What does a risk-based approach to prioritise implementation of mitigations mean?
A risk-based approach simply means you don’t fix every vulnerability in the same order, you focus on the issues that pose the greatest risk first.
When vulnerabilities are discovered (for example, through a penetration test or vulnerability scan) you can assess the likelihood of exploitation together with the impact to assign a risk rating to the issue.
In most organisations, this is combined with a remediation policy that sets timeframes for addressing vulnerabilities. For example:
- Critical: Fix within 1 week
- High: Fix within 3 weeks
- Medium: Fix within 6 weeks
- Low: Fix as part of regular maintenance
What Policies are Required for ST4S?
This brings us to organisational policies requirements.
What is a Policy?
At a high level a policy just summarises all the rules that your organisation needs to follow to comply with laws, standards and any other expectations you may maintain.
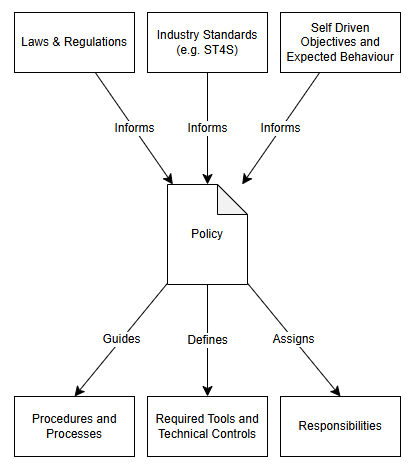
Once you have defined a policy you can then implement various controls to meet your policy.
What Key Organisational Policies does ST4S require?
Broadly speaking, the Safer Technologies for Schools (ST4S) framework’s policy requirements are subsets or simplifications of established industry standards like ISO 27001.
Here are some key areas to start defining:
- Information Security Policy: Broadly cover your organisation's overall commitment and direction for maintaining confidentiality, integrity, and availability of information systems. The policy may outline controls like access control, incident response, patching, and mobile device management.
- Data Retention & Deletion Policy: Define how long data is kept and the secure methods used for deletion. Especially wrt. data collected that you no longer need to store (e.g. inactive accounts).
- Privacy Policy: Describe what data you collect, use, and disclose to third parties.
Project Black can Help
Project Black is an Australian penetration testing firm and cybersecurity consultancy with experience delivering engagements for edtech providers seeking to complete the Safer Technologies for Schools (ST4S) assessment.
Get in touch for a chat about how we can support your ST4S journey.

