Password Policy GPO
We routinely crack 40% of passwords in a given Active Directory environment once we obtain Domain Admin. Updating the password policy to protect against modern password cracking techniques is one way to enforce better password usage in your environment.
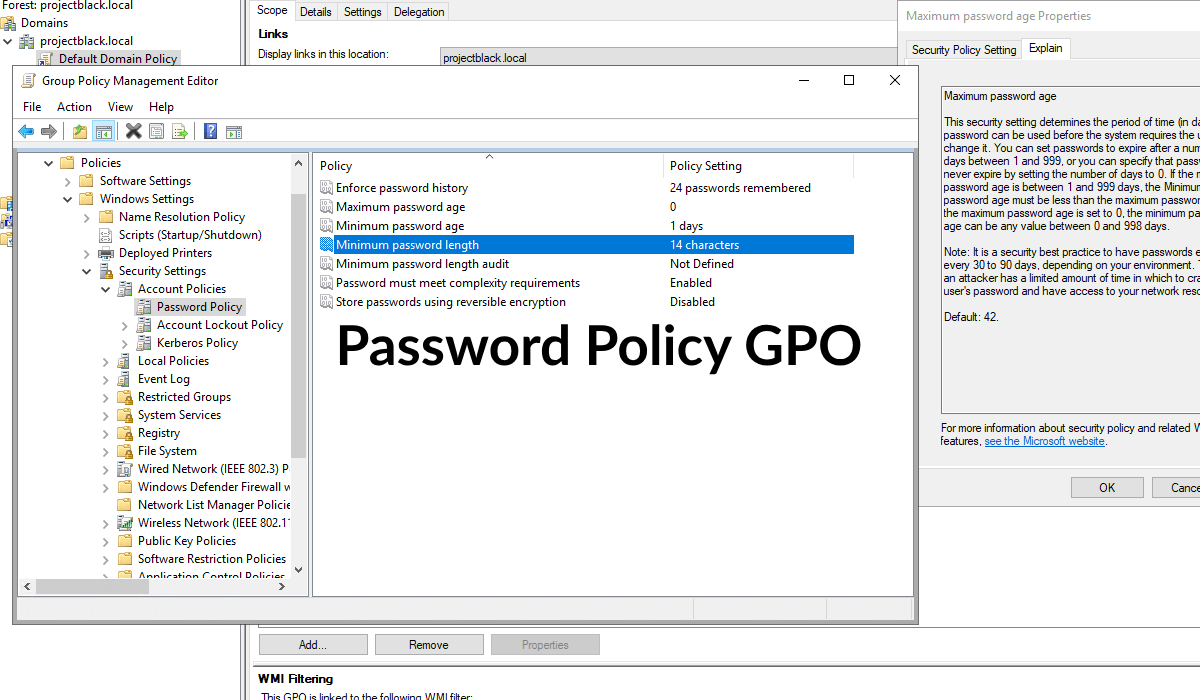
The Typical Problem
People are bad at creating passwords.
Take something like Melbourne2025!. On the surface this may look like a strong password, it meets password complexity requirements and is 14 characters long.
In practice, this password would take seconds to crack offline.
Modern password cracking tools are built to take advantage of human behaviour. A capitalised word, a few numbers tacked on the end and a special character for good measure (sometimes).
The GPO
Changing the Default Domain Policy is sufficient in most environments unless you're looking at Fine Grained Password Policies (policies which can be applied to Security Groups).
The relevant policy setting can be found at:
Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Account Policies -> Password Policy
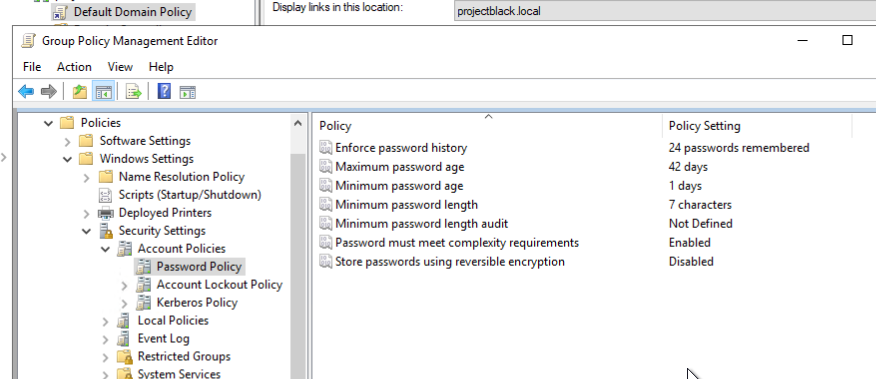
Here's what we recommend you set:
- Maximum password age: 0, don’t force passwords to expire.
- This lines up with NIST guidance, which says regular expiry can actually make things worse by encouraging predictable changes.
- Minimum password length: Set it as high as you can realistically get management to agree to.
- Aim for something like 16 characters if you can and combine it with user awareness training about passphrases.
Impact
Updating this GPO has zero (0) direct impact. It will only apply when a user tries to change their password.
To force users to update their password to comply, you can set the "User must change password at next logon" flag for users but we'd recommend you conduct some basic user awareness training prior to doing this.
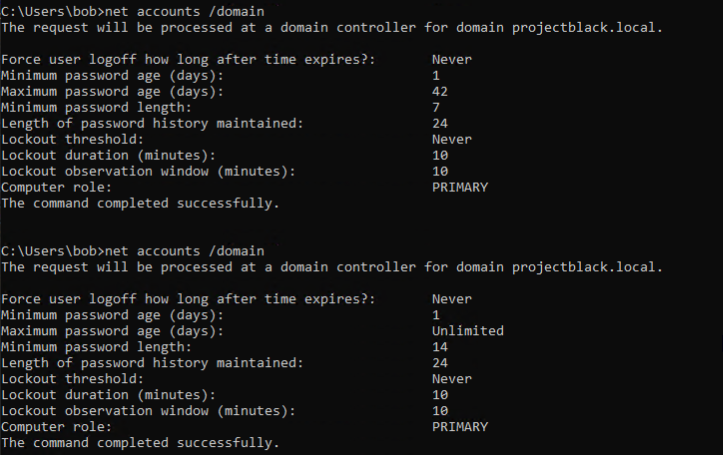
Validation
Once deployed, net accounts /domain can be run to observe the effects of the applied policy.
Educating Users
User education is the other key piece of the puzzle. In environments where they've combined strong minimum password requirements with training, we’ve seen password crack rates drop to as low as 5%.
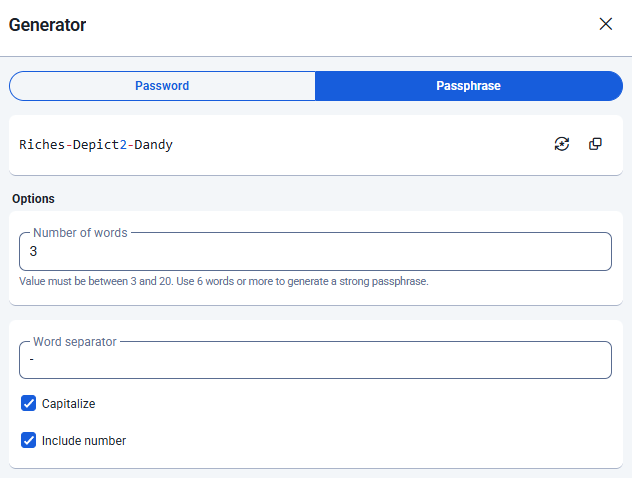
It might seem like we could just take every word in the dictionary, generate every possible permutation, and eventually crack the password. But in reality, the entropy introduced by long passphrases makes that approach pretty infeasible.
Other Common Password Related Issues
During our penetration tests, we often come across two other common (and risky) behaviours:
Sharing Passwords between Normal and Admin Accounts
One we see far too often: users reusing the same password for both their regular user account and their admin account. This completely undermines the purpose of account separation. If one account gets compromised, so does the other.
That’s a fast track to full environment access for an attacker.
End User Accounts Sharing Passwords
This one usually stems from the onboarding process. A common pattern is IT creating accounts and setting the initial passwords but not enforcing a password reset at first logon.
The result is multiple staff using the same password increasing the chance of lateral movement in the environment when a single user account is breached.

