Free Web Filtering
Free, simple, and effective. DNS based web filtering is a security control every organisation should consider. It adds a layer of protection with minimal effort and no additional cost.
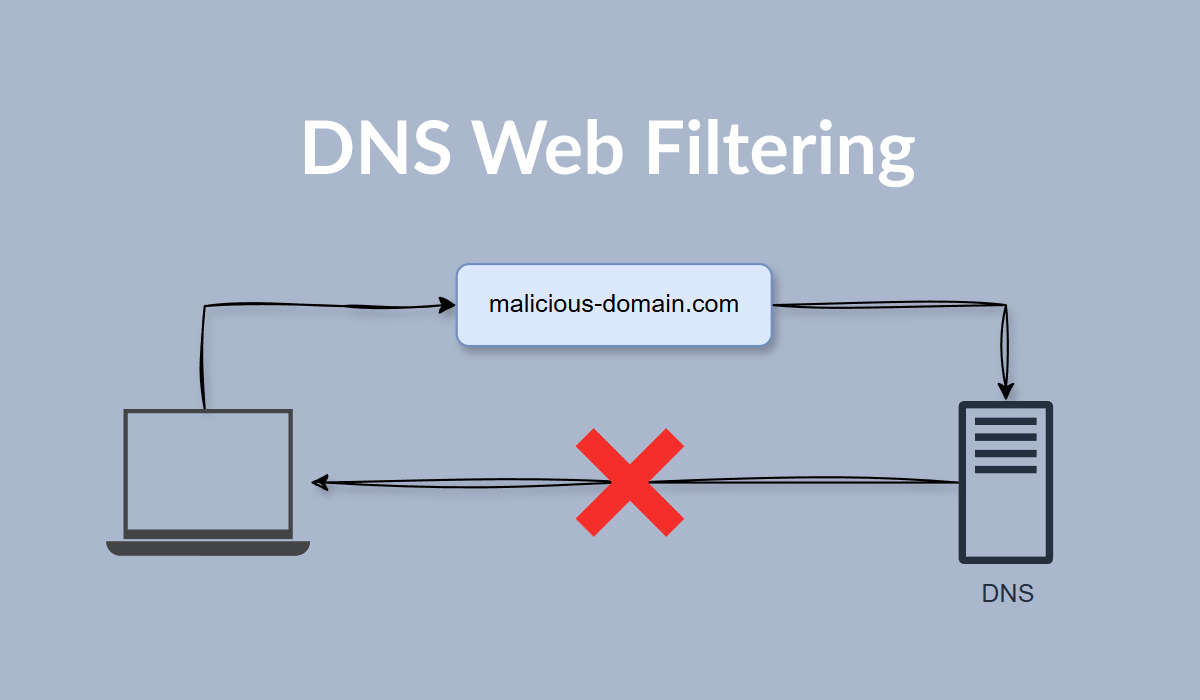
If you haven’t heard of DNS-based web filtering, it’s a simple but powerful security control that’s easy to overlook. Traditional DNS servers resolve any domain name they’re asked to. Security-focused DNS providers use threat intelligence to block known malicious domains by not allowing them to be resolved.
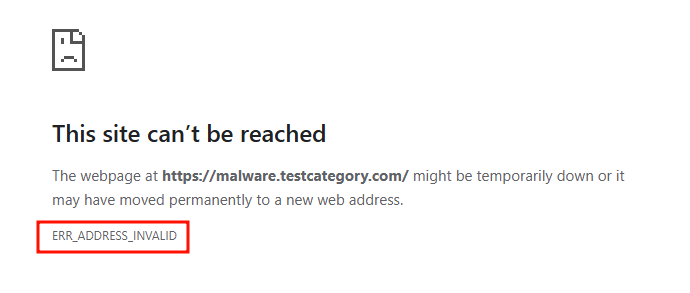
We can demonstrate this by using a test domain. malware.testcategory.com
Using a security focused DNS server the result is that the domain gets resolved incorrectly to 0.0.0.0 (non-routeable).
dig malware.testcategory.com @1.1.1.3
;; ANSWER SECTION:
malware.testcategory.com. 60 IN A 0.0.0.0
# This would normally resolve to something else!
dig malware.testcategory.com @1.1.1.1
;; ANSWER SECTION:
malware.testcategory.com. 60 IN A 104.18.4.35
malware.testcategory.com. 60 IN A 104.18.5.35This means that if malware attempts to contact a command-and-control server or download additional payloads from a flagged domain, the DNS request will fail and thus the subsequent connection attempt will fail. It’s a low-effort, cost-free way to reduce exposure to common threats, and can be deployed across your organisation in minutes.
Limitations
Of course, there are limitations!
If you're facing a targeted attack by a human adversary, they can easily bypass DNS filtering by using IPs directly or using new domains that haven't yet been flagged.
That said, it's still a valuable control against opportunistic threats and off-the-shelf malware and provides a basic level of protection.
Implementation
For this guide, we'll be using Cloudflare's Malware and Adult Content blocking DNS servers. 1.1.1.3 and 1.0.0.3 however the process is the same regardless of provider choice.
Router Configurations
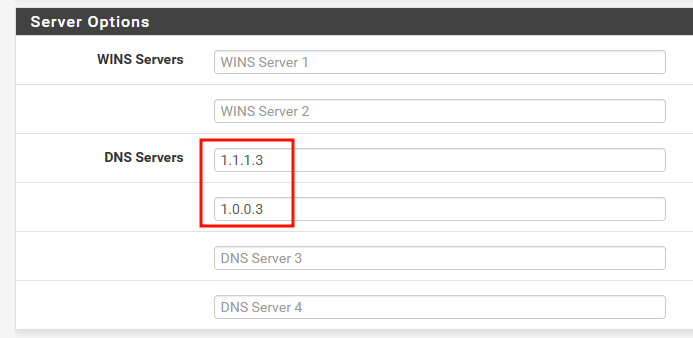
One of the easiest ways to roll out DNS filtering across an entire network is by updating your router's DHCP settings. By setting the DNS server options to point to a security-focused provider all devices that receive their network configuration via DHCP will automatically use the filtered DNS service.
The screenshot below shows changing that setting in the DHCP servers section on a pfSense device.
The details may vary depending on what router you user but generally the steps will involve:
- Logging into your router’s web interface
- Navigating to the DHCP server or LAN settings
- Updating the DNS server fields to use your preferred filtering provider (e.g. OpenDNS, Cloudflare for Families, or Quad9)
- Saving the changes and restarting the router if required
This method requires no changes on individual devices and extends protection to printers, IoT devices, and other network-connected equipment that typically lack traditional endpoint security.
Active Directory Environments
In Active Directory environments, most devices rely on domain controllers for DNS resolution. In this case, the recommended approach is to configure DNS forwarders on the domain controllers to point to your chosen filtering provider, rather than relying on root hints.
In DNS Manager, right click your DNS servers and click Properties.
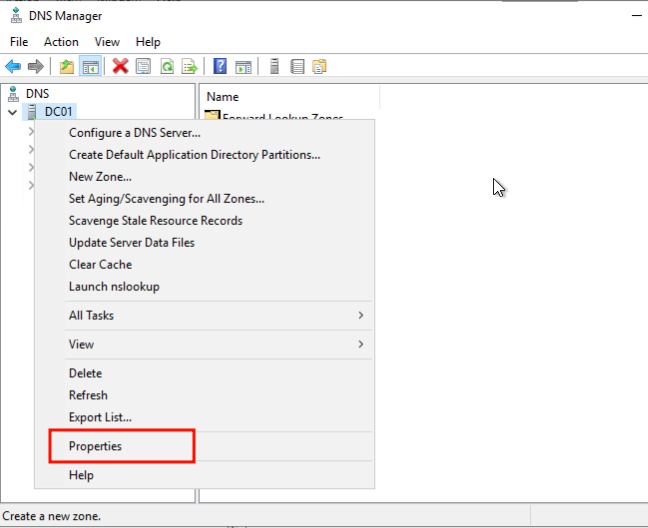
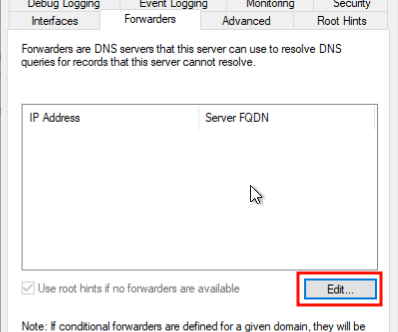
Use the Forwarders -> Edit section to add our security focused DNS providers.
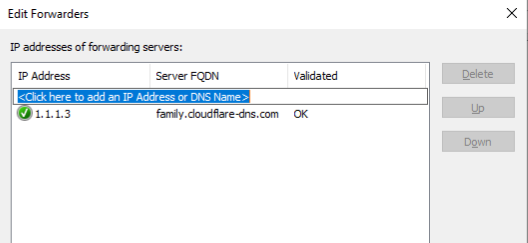
Once DNS forwarders are configured, every device that uses the domain controllers for DNS resolution will automatically benefit from the protection.
Roaming Workstations
The sharp-eyed will notice a gap in coverage, roaming workstations won't be protected once they leave the networks where the above settings have been configured.
While it might seem straightforward to hard-code secure DNS servers on workstations, this approach breaks internal name resolution when the device is back on the network.
Script
A simple solution is to use a script that dynamically updates the device’s DNS settings based on its network context. When the workstation is off-network, the script applies secure DNS servers. When it returns to the corporate network, it reverts to using the DNS servers provided by the DHCP server, typically your internal domain controllers.
# Define internal DNS suffix and external secure DNS servers
# Replace corp.local to match your internal domain suffix provided by DHCP server
$internalSuffix = "corp.local"
$externalDNS = @("1.1.1.2", "1.0.0.2")
# Get all active physical adapters
$activeAdapters = Get-NetAdapter | Where-Object {
$_.Status -eq 'Up' -and $_.HardwareInterface -eq $true
}
# Collect DNS client configurations for these adapters
$dnsClientConfigs = foreach ($adapter in $activeAdapters) {
Get-DnsClient | Where-Object { $_.InterfaceIndex -eq $adapter.InterfaceIndex }
}
# Determine if we're on internal network
$onInternal = $dnsClientConfigs | Where-Object {
$_.ConnectionSpecificSuffix -eq $internalSuffix
}
# Set DNS based on location
foreach ($adapter in $activeAdapters) {
if ($onInternal) {
# Reset to automatic DNS (DHCP)
Set-DnsClientServerAddress -InterfaceIndex $adapter.InterfaceIndex -ResetServerAddresses
} else {
# Apply secure public DNS
Set-DnsClientServerAddress -InterfaceIndex $adapter.InterfaceIndex -ServerAddresses $externalDNS
}
}This script needs to run every-time a network change is detected. We can create a scheduled task to achieve this.
Scheduled Task
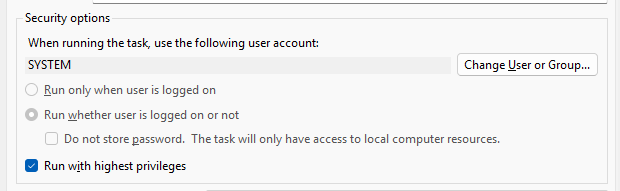
Security Options
Run task as: SYSTEM
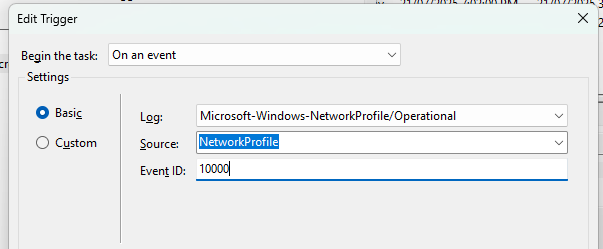
Trigger
To trigger it we can listen for Event ID 10000 which is an event that fires every time a network is connected.
Action
If low privilege users can edit this script, they can leverage it to elevate their privileges.
Program/script: powershell.exe
Add arguments (optional): -nologo -noninteractive -noprofile -ExecutionPolicy Bypass -file C:\scriptpath\dns.ps1
Alternative Providers
Cloudflare is one of the few providers who offer free security focused DNS services.

I've linked a couple of the other options below for your consideration.