Unveiling a Task Scam Empire
A month ago, I signed up for a scam. Little did I know, this rabbit hole would ultimately lead to uncovering a large scale operation, a report filed with the ACSC and a subsequent an investigation by the NSW police.
Scambaiting has emerged as an intriguing and informative practice, captivating the attention of many, including myself (special shoutout to @kitboga). The opportunity to actively engage in scambaiting presented itself recently, and I couldn't resist delving into this captivating world.
Beyond the entertainment value, by deconstructing and reporting on these scams, we can shed light on the social engineering tactics used by cybercriminals and raise awareness about the potential dangers they pose.
Act One: Onboarding
It was a normal Tuesday morning when I received an interesting message on WhatsApp.
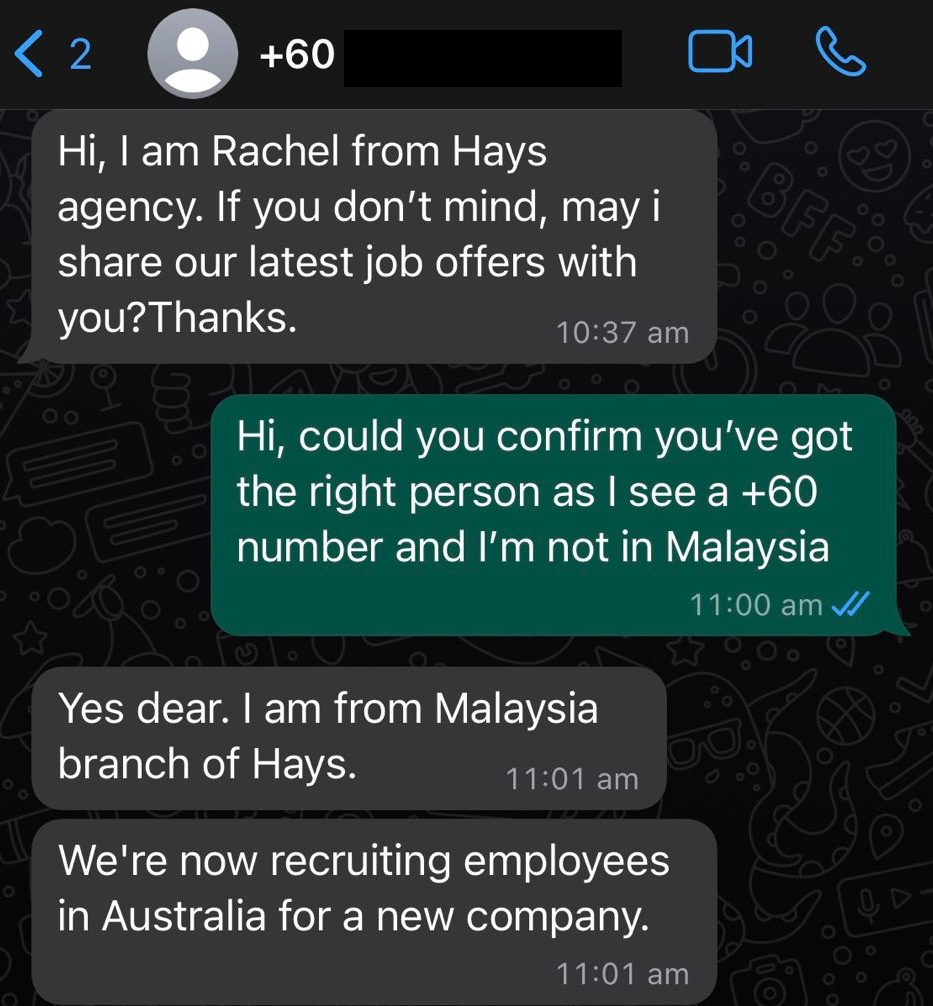
A job offer from someone overseas, via WhatsApp, what could possibly be off with this? I agreed to proceed and shortly after, a separate Australian phone number sent me a message.
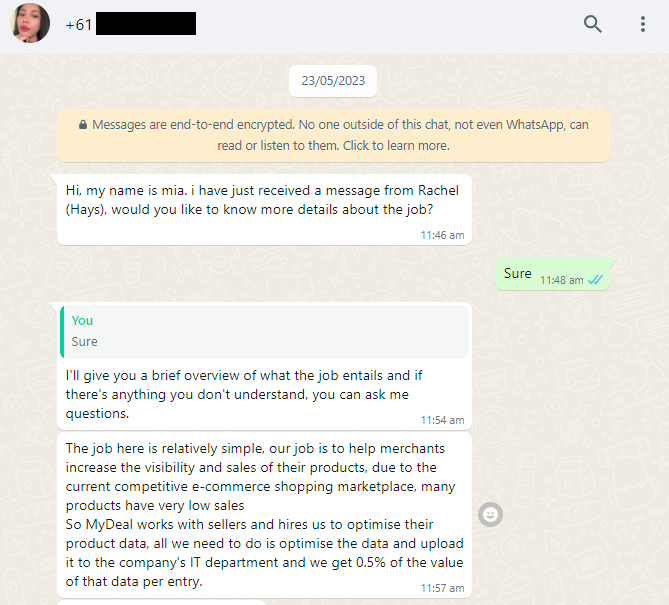
"Mia" explained to me that:
- The company in question was hiring people to perform "boosts".
- "We spend 30-60 minutes a day on MyDeal providing a platform to complete 60 data boosts and earn 0.5% per data, which can be withdrawn upon completion of all data."
- There's a commission incentive to complete the boosts quickly and consecutively over multiple days.
- "It only takes 30-60 minutes to complete a 60/60 lift and you can earn at least A$80-100 per day (depending on your ability)."
- "A$50 is a fixed salary and A$300, A$1,000 and A$3,000 are incentives for ongoing work and you can organise your own hours each day."
Interestingly, they even went to the effort of doctoring some convincing images to make people believe they were dealing with the actual company, MyDeal in this case.

After a few more exchanges, I finally had access to the platform.

If the alarm bells haven't already been blaring, they should be ringing loudly and urgently.
🚩 Mentions of cryptocurrencies are not common in most legitimate jobs.
🚩 The use of a .online domain instead of the company's official domain.
Act Two: Understanding the Scam
With access to the platform, I can now begin to start dissecting how this scam actually works.
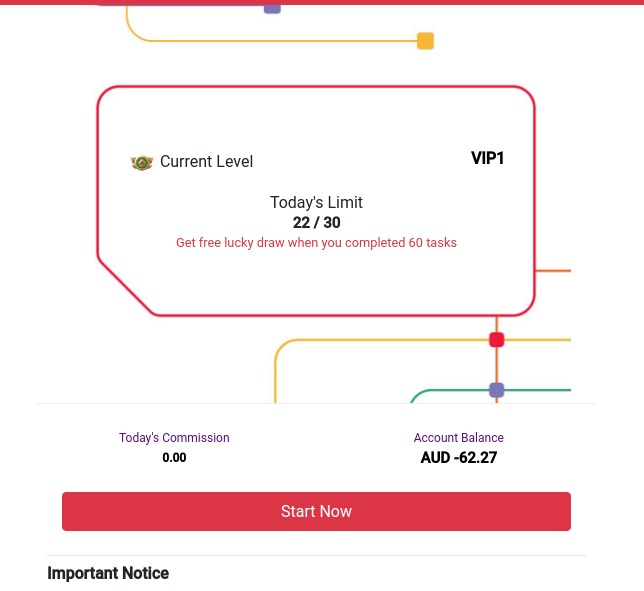
Upon accessing my account, I made a curious observation—a balance of $20 was already present. However, the process of "withdrawing" this amount appeared to have two specific requirements:
- The account needed to have a minimum balance of $50.
- A minimum of 30 "Tasks" need to have been completed for the day.
At this point, I encountered another hurdle. I realized that I couldn't start my assigned "Tasks" as it necessitated a minimum balance of $30. Interestingly enough, this requirement seemed deliberately designed to allow the scammers to establish a sense of trust and familiarity before asking victims to deposit funds.
This is where Mia comes back into the picture. She willingly grants me access to her account, which conveniently boasts a balance of approximately $1000. This access allows me to gain firsthand experience and familiarity with the scam's operations and processes.
I also receive my first clue regarding the scam's money extraction tactics, as revealed in the bolded text below:
I have already registered, you can now log out of your account and log in to mine to start getting familiar with the process of this work, in which you will receive 25% commission.
During the familiarization process, you let me know if you encounter a negative number that you cannot pass, because it means receiving bonus mission that will earn you five times the commission upon completion
The Actual Tasks
Once I begin working on Mia's account, I find that the actual tasks are trivial in nature. It merely involves grabbing an "order" and clicking the submit button. There are no complex schemes involving affiliate linking or ad clicking. Instead, it appears to be a purposeless task designed solely to keep users engaged and maintain the illusion of legitimate work.
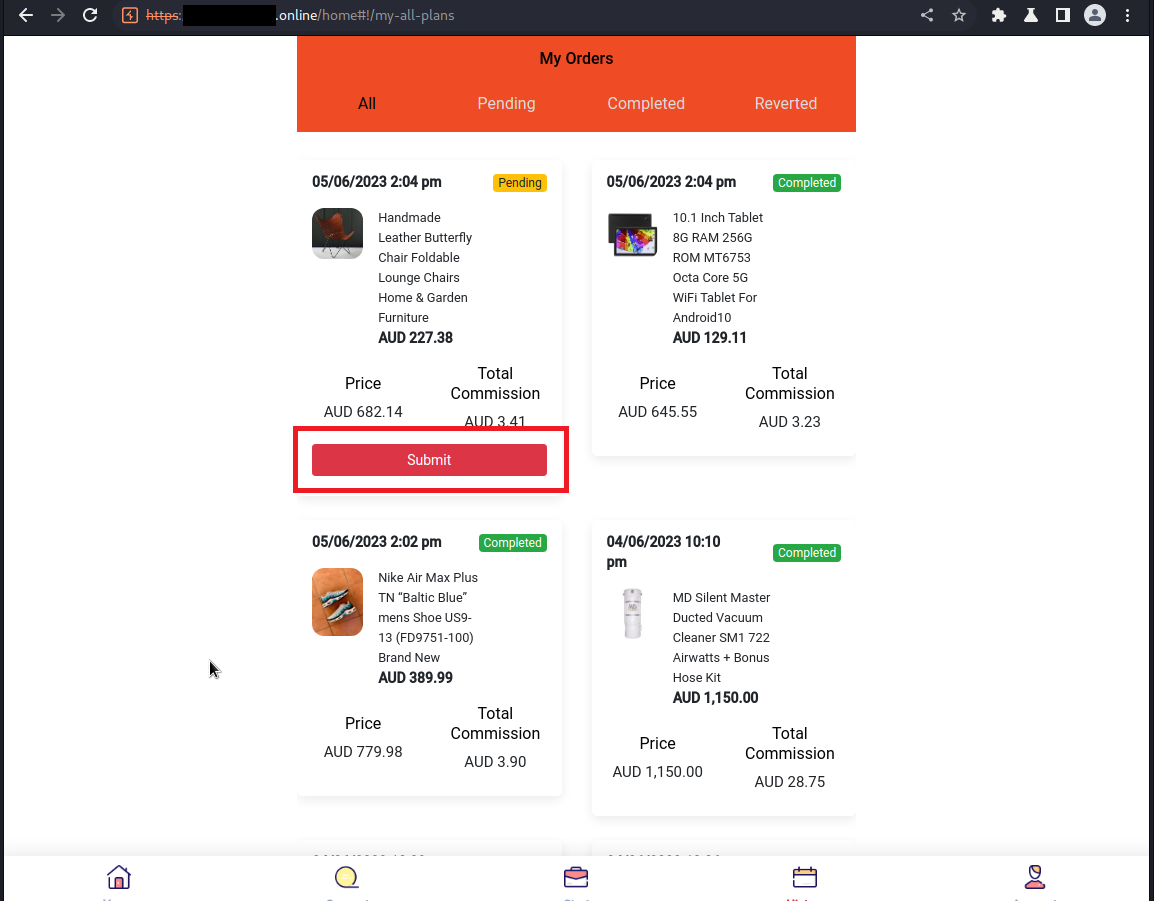
Before I can successfully complete my quota of 30 tasks for the day, I encounter the negative balance scenario that Mia had previously described.
Mia directs me to contact Customer Service, providing a third WhatsApp number, which is likely operated by the scammers themselves. The purpose of this contact is to facilitate a deposit process, as demonstrated by Mia using her own account.
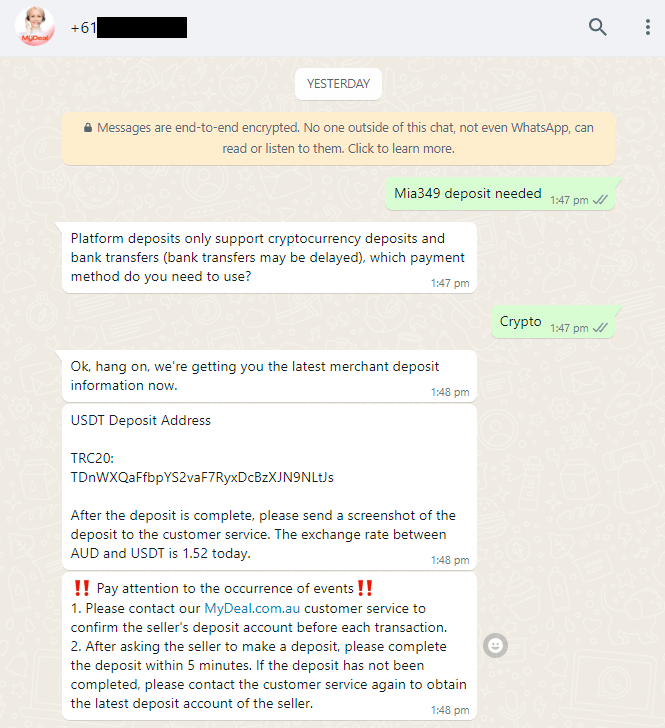
In the next phase of the scam, Mia supposedly sends some USDT (cryptocurrency) to the provided address. She then requests that I provide a screenshot of the successful transfer as evidence to support the transaction.
Upon completing this step, Mia's account suddenly gains the ability to complete the 30 tasks for the day. As a final touch to reinforce the illusion of profitability, she proceeds to perform a withdrawal, demonstrating that she has indeed made money from the scam.
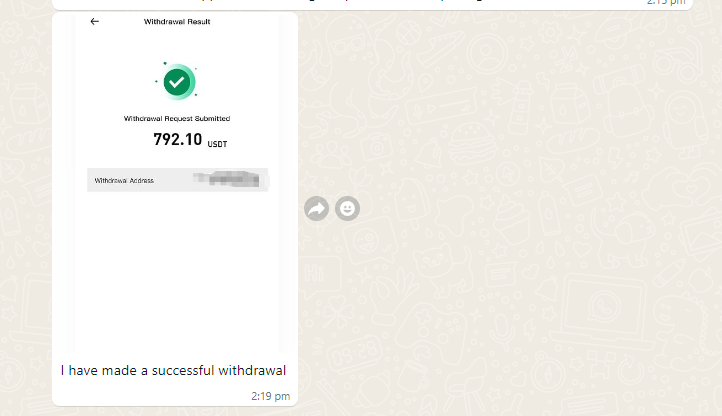
I have now been sold the dream. Conveniently my account now has enough balance in it to start the tasks due to the "commission" earned from working on Mia's account.
TL;DR:
To summarize how the scam works.
- When attempting to complete the required 30 tasks, users encounter a negative balance (known as a bonus mission).
- Scammers prompt victims to deposit money to clear the negative balance, promising increased earnings (e.g. victims may expect to earn back more than they deposit if they can get to 30/30).
- The functionality of withdrawals from the platform remains uncertain, but scammers likely allow some withdrawals to entice victims to invest further.
- The scam fosters a compounding effect, tempting victims to continue participating by promising higher rewards if they complete tasks over multiple days.
While it may seem surprising, the unfortunate reality is that people do fall victim to scams like this. My first Google search surfaced the following article.

Act Three: Exposing and Reporting Them
In a surprising turn of events, the scammers managed to leave their administration portal unsecured...
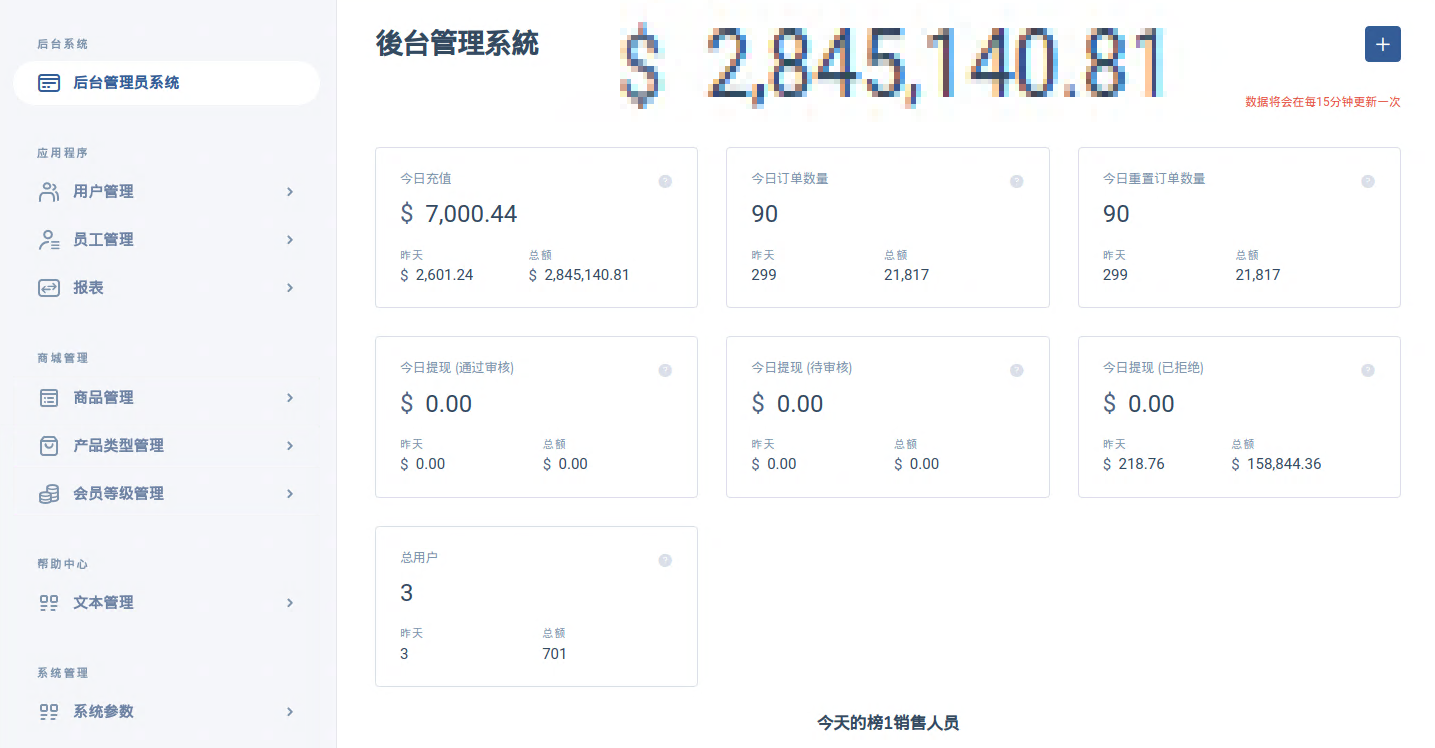
Upon opening the portal, the numbers immediately presented are quite upsetting.
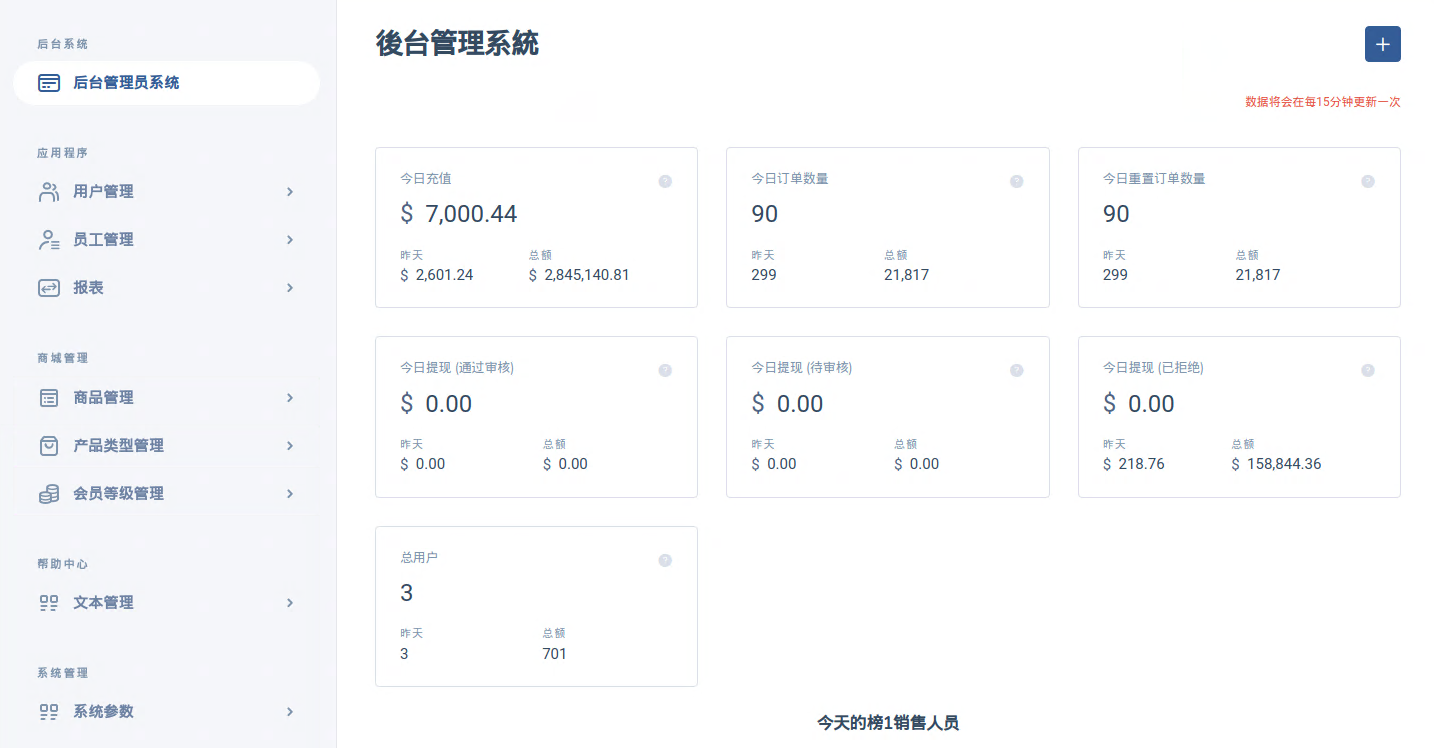
If these numbers are legitimate, the first box indicates that on the day this screenshot was taken, $7000 was received in deposits by the scammers with lifetime deposits totaling $2,845,140.
Unearthed are an array of tools that aid in running the scam seamlessly. Their tooling allows them to create detailed reports, and closely track user behavior/stats. Furthermore, there appears to be functionality which permits customization of the platform (presumably to reskin the user interface for other scams, more on this later).
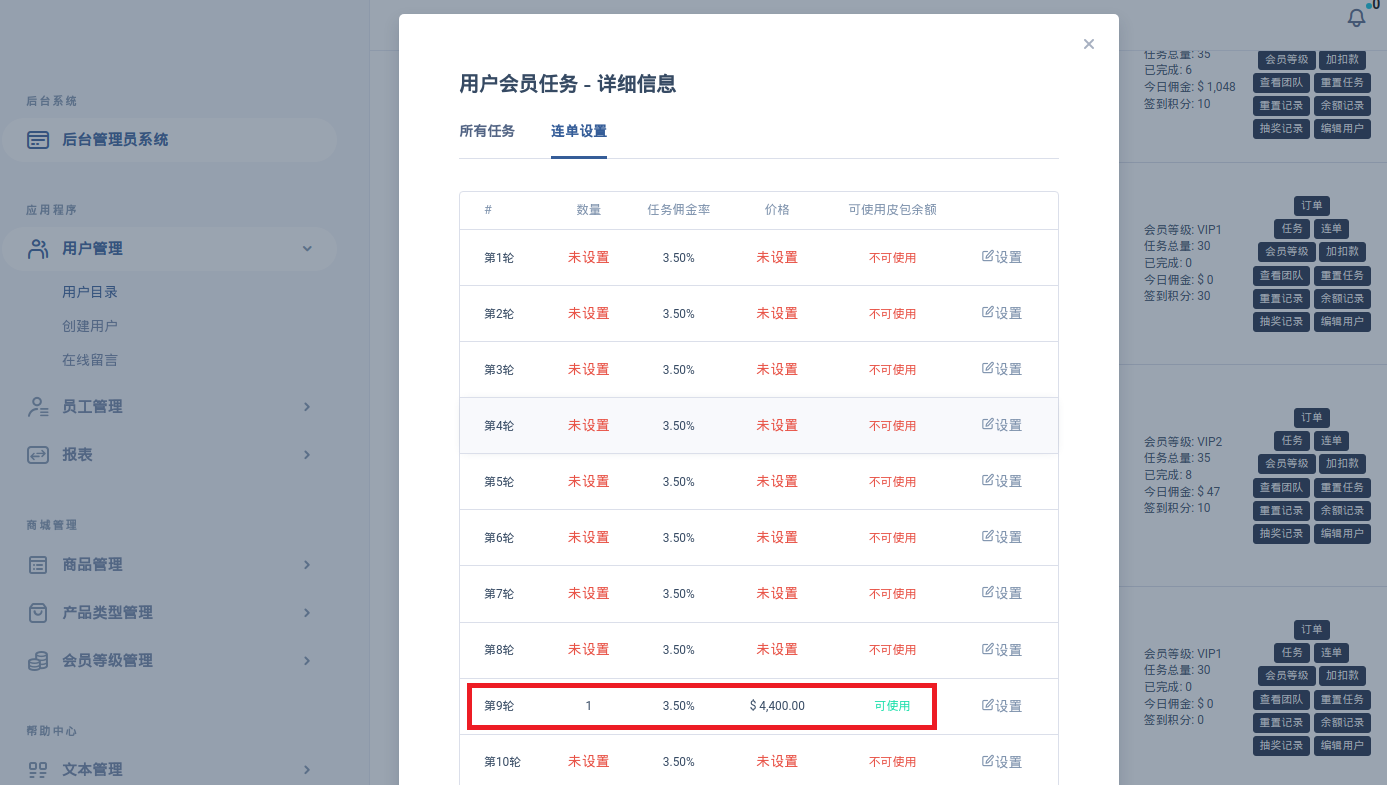
Poking around a bit more we eventually find the menu used by the scammers to configure "bonus missions" for victims.
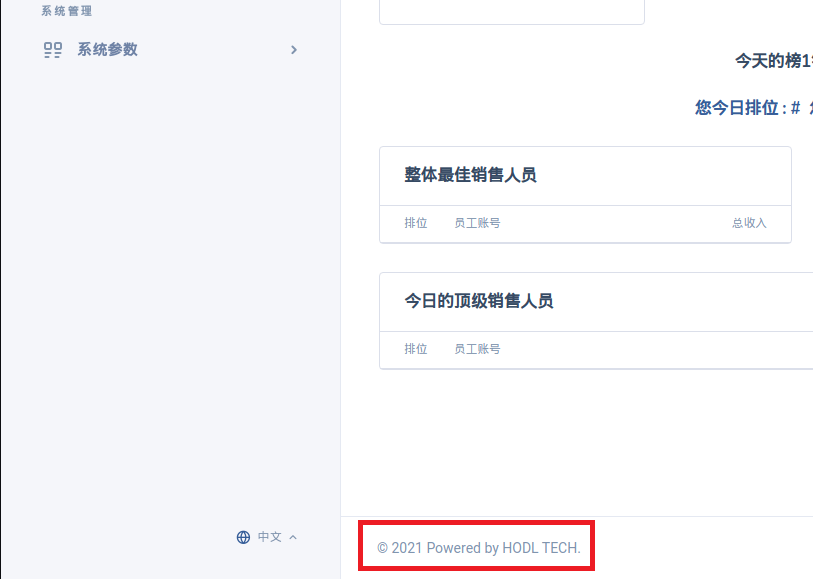
A final interesting discovery as I click around — a curious copyright notice for "HODL TECH." I can't help but wonder if the companies I find on Google associated with this name have any connection to the scam I'm unraveling.
Then There Were Two
The thought that these scammers might be operating under multiple guises crossed my mind as their tooling seemed to allow for significant customization.
I decided to take a look around and without much effort I found this.
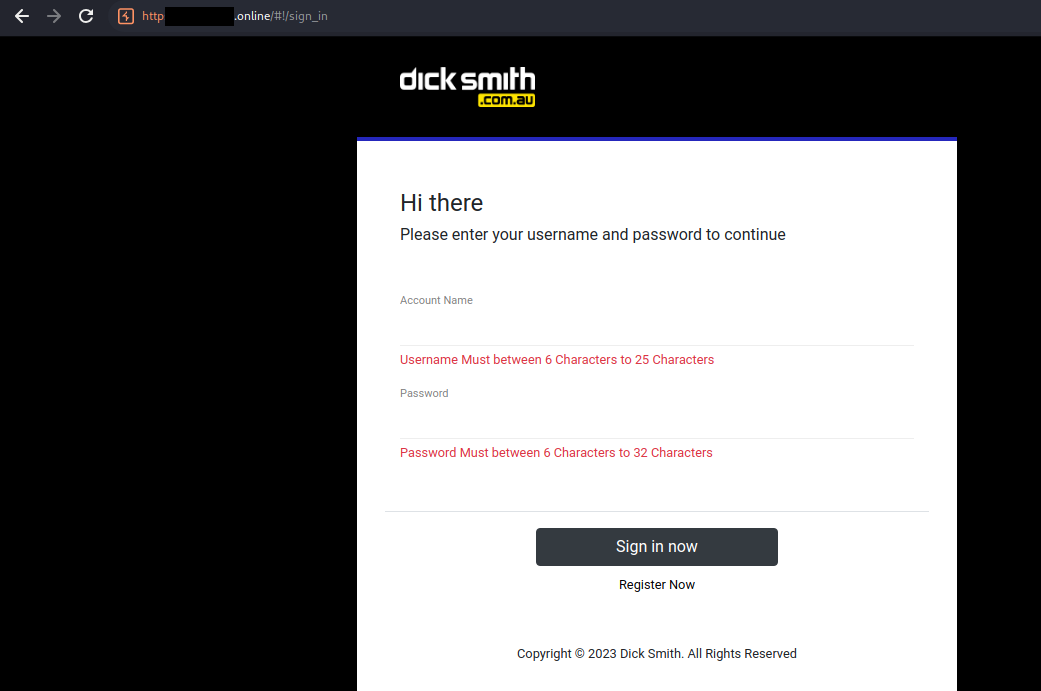
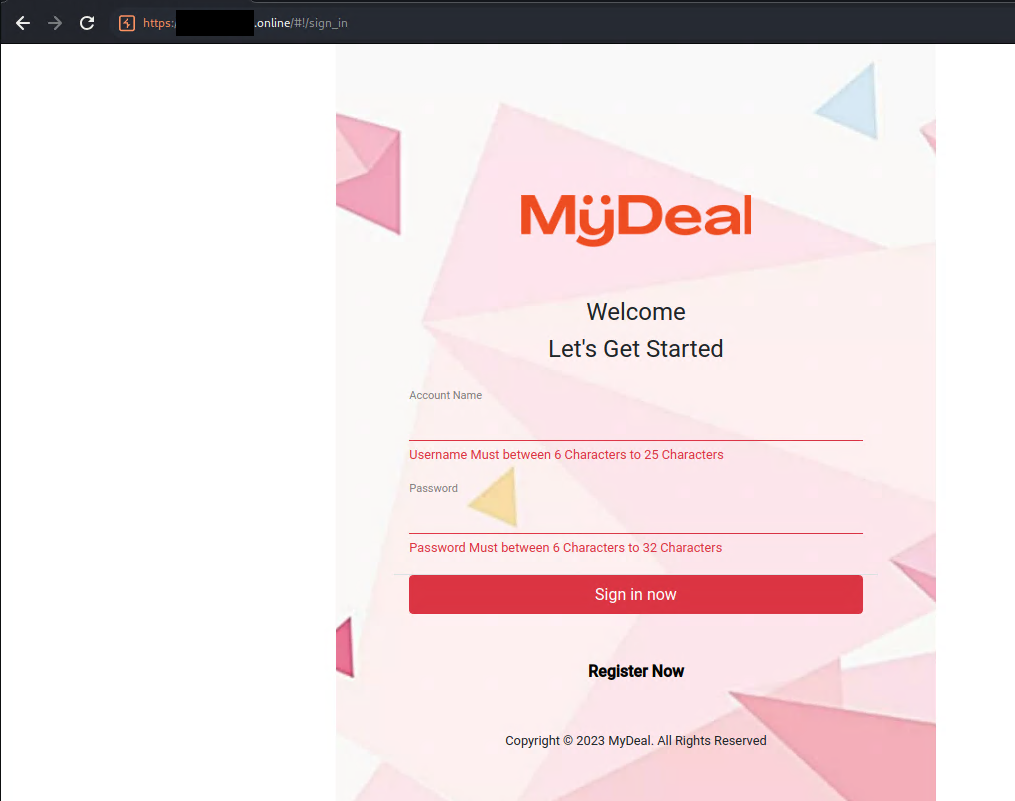
Look familiar? The same group of people seemed to be running another task scam impersonating Dick Smith.
This was ultimately confirmed when I found that the same administration tools for this domain/host were also left unsecured...
Reporting Them
Armed with substantial evidence, I felt compelled to report these scammers and their activities to the authorities. With phone numbers, insights into their tooling, and knowledge of their primary bank account, I figured that at the very least, victims in their user database could be contacted to prevent further losses.
But, the response from the police fell a bit short of expectations, as they chose to focus solely on a domain take down. I'm hoping that they are just too busy tackling larger scale crimes.

These scammers likely have more than just the two domains I have found and they will undoubtedly just purchase new domains and continue about their way.
At least 1 of the 2 domains reported has been taken down as of time of writing.

Conclusion
In the quest to deconstruct and report this deceitful task scam, I uncovered some of the manipulative tactics employed by its perpetrators.
Although reporting the scam had limited impact, I'm hoping that documenting this experience can help raise awareness.
Awareness is a key part of prevention and if cyber security awareness training or other cyber education solutions are of interest to your organisation, please do not hesitate to reach out to us.


