Disable TLS 1.0 and 1.1 via GPO
Disabling TLS 1.0 and 1.1 via GPO strengthens security by removing outdated protocols. While practical exploitation is difficult, turning them off is often easier than justifying scan findings to auditors. Here’s how.
Here's what a default install of Windows Server 2019 looks like when we run nmap -sV --script ssl-enum-ciphers host-ip against it.
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-03-27 18:12 AEDT
Nmap scan report for 192.168.2.254
Host is up (0.0017s latency).
Not shown: 987 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-03-27 07:11:27Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: projectblack.local, Site: Default-First-Site-Name)
| ssl-enum-ciphers:
| TLSv1.0:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (secp384r1) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (ecdh_x25519) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_3DES_EDE_CBC_SHA (rsa 2048) - C
| compressors:
| NULL
| cipher preference: server
| warnings:
| 64-bit block cipher 3DES vulnerable to SWEET32 attack
| TLSv1.1:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (secp384r1) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (ecdh_x25519) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_3DES_EDE_CBC_SHA (rsa 2048) - C
| compressors:
| NULL
| cipher preference: server
| warnings:
| 64-bit block cipher 3DES vulnerable to SWEET32 attack
| TLSv1.2:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (secp384r1) - A
| TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (ecdh_x25519) - A
| TLS_DHE_RSA_WITH_AES_256_GCM_SHA384 (dh 2048) - A
| TLS_DHE_RSA_WITH_AES_128_GCM_SHA256 (dh 2048) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (secp384r1) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (secp384r1) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (ecdh_x25519) - A
| TLS_RSA_WITH_AES_256_GCM_SHA384 (rsa 2048) - A
| TLS_RSA_WITH_AES_128_GCM_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_256_CBC_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_128_CBC_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_3DES_EDE_CBC_SHA (rsa 2048) - C
| compressors:
| NULL
| cipher preference: server
| warnings:
| 64-bit block cipher 3DES vulnerable to SWEET32 attack
|_ least strength: C
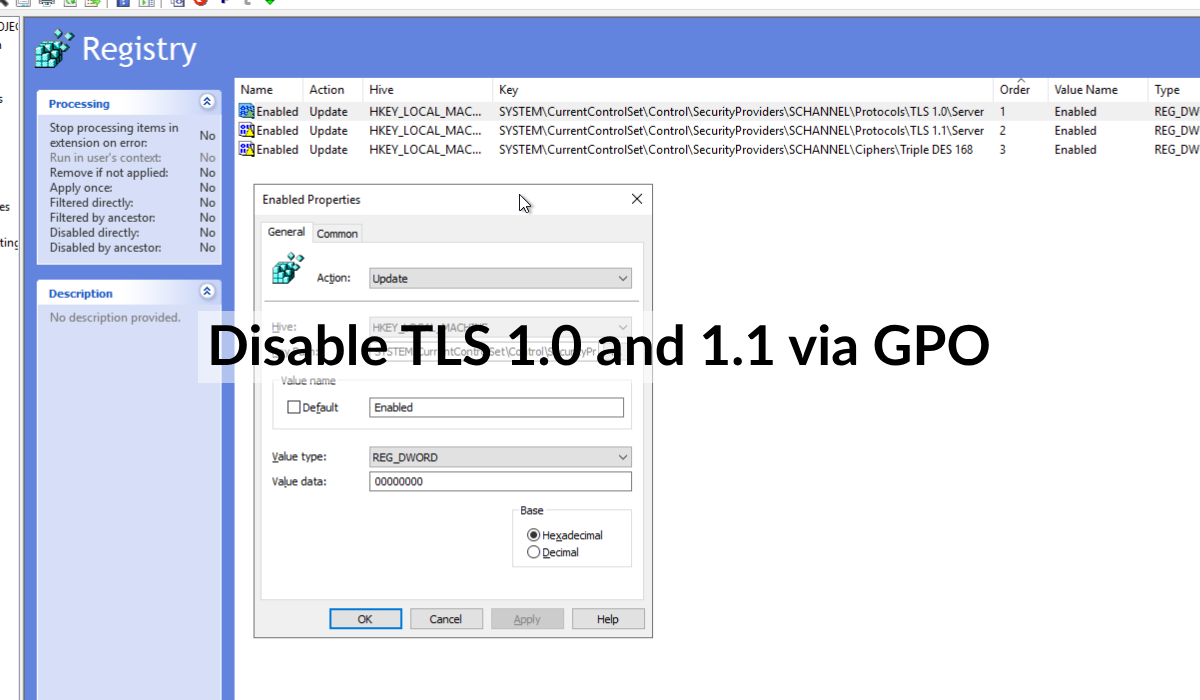
... SNIP ...To disable TLS v1.0 and TLS v1.1 on Windows hosts (for applications that don't implement their own TLS and don't use Schannel SSP) we need to set the following registry keys:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server- Value Name:
Enabled - Value Type:
DWORD - Value Data:
0
- Value Name:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server- Value Name:
Enabled - Value Type:
DWORD - Value Data:
0
- Value Name:
While you're here, consider disabling Triple DES as well as it's considered weak due to its shorter effective key length and will show up as a warning in most vulnerability scanner or penetration test reports as a SWEET32 vulnerability.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\Triple DES 168- Value Name:
Enabled - Value Type:
DWORD - Value Data:
0
- Value Name:
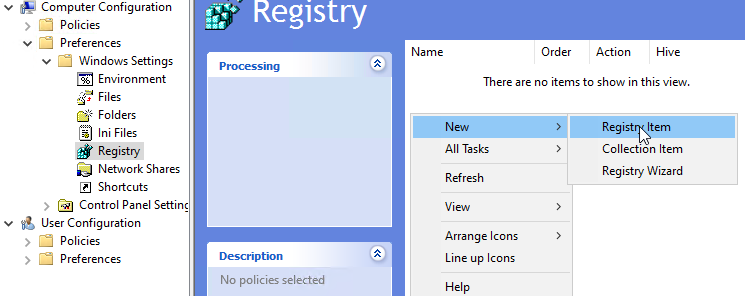
To create GPOs which set registry keys you need to navigate to Computer/User Configuration -> Preferences -> Windows Settings -> Registry and create new registry items.
Then select the HKEY_LOCAL_MACHINE hive and paste the key path and other variables into their relevant spots.
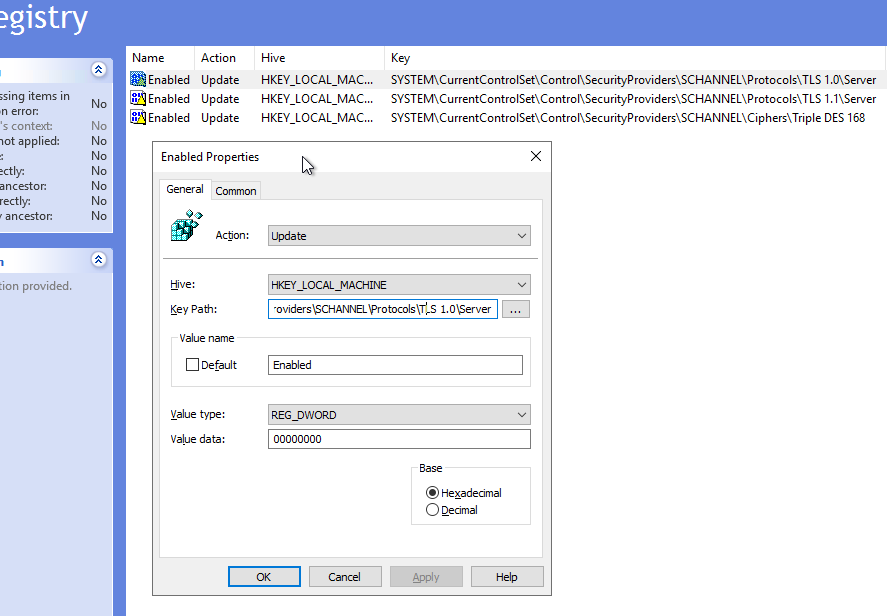
This GPO can then be rolled out across computers in pilot groups.
Potential Impacts
- Clients may still attempt to use the deprecated protocols if required - this may be desired behaviour though so continue reading if it's not.
- Deploying this GPO only disables TLS 1.0 and 1.1 for services running on the host (server-side).
- It does not restrict the host’s ability to act as a client connecting to other systems using TLS 1.0 or 1.1.
A server with this GPO applied will no longer accept TLS 1.0/1.1 connections to its services (e.g., a web server, email server, or API).
However, the same server could still initiate outbound TLS 1.0/1.1 connections to other systems (e.g., connecting to an external legacy API or third-party service that is outside of your control).
- Clients or applications that can’t use TLS 1.2 will not connect to services on hosts with this GPO applied. Examples include:
- Applications that use old software frameworks - Java (versions before 8) or .NET (versions before 3.5).
- Older operating systems - < Windows 7
Testing Again
Here's what the same scan from earlier looks like now.
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-03-29 11:26 AEDT
Nmap scan report for 192.168.2.254
Host is up (0.00079s latency).
Not shown: 987 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-03-29 00:25:18Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: projectblack.local, Site: Default-First-Site-Name)
| ssl-enum-ciphers:
| TLSv1.2:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (secp384r1) - A
| TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (ecdh_x25519) - A
| TLS_DHE_RSA_WITH_AES_256_GCM_SHA384 (dh 2048) - A
| TLS_DHE_RSA_WITH_AES_128_GCM_SHA256 (dh 2048) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (secp384r1) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (secp384r1) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (ecdh_x25519) - A
| TLS_RSA_WITH_AES_256_GCM_SHA384 (rsa 2048) - A
| TLS_RSA_WITH_AES_128_GCM_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_256_CBC_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_128_CBC_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A
| compressors:
| NULL
| cipher preference: server
|_ least strength: A
... SNIP ...Disabling Client Side TLS 1.0 and 1.1
If your goal is to tidy up vulnerability scan reports, disabling client-side TLS 1.0 and 1.1 isn’t strictly necessary.
But if you’re considering disabling client-side protocols, proceed carefully.
Disabling client-side TLS 1.0 and 1.1 means your systems will refuse to connect to any external service that hasn’t adopted TLS 1.2+. Unlike your own servers, you can’t force external systems to upgrade. If a critical service still uses TLS 1.0 or 1.1, your only fix is to revert the change which can cause a lot of headaches.
The relevant registry keys to do this are listed below, these can be deployed in a GPO using the same method documented above.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client- Value Name:
Enabled - Value Type:
DWORD - Value Data:
0
- Value Name:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client- Value Name:
Enabled - Value Type:
DWORD - Value Data:
0
- Value Name:
Recommendation
Tackle server-side first: Roll out the server-side GPO and monitor for issues. This isolates problems to clients that don't support TLS1.2.
From here you can deploy a subsequent GPO to block client side TLS 1.0 and 1.1 which for the most part will only highlight any external service you depend on doesn't support TLS 1.2+.

