Disable LLMNR via GPO (Together with NBT-NS and MDNS)
You're probably reading this because some pentesters got Domain Admin using LLMNR as a part of their attack chain in your internal network. Here's a quick tutorial for how to disable it via GPO.
When DNS resolution fails (e.g. someone types a server name wrong), Windows falls back to LMNR, NBT-NS and MDNS to ask other devices on the network to see if the request can be resolved.
While well-intentioned, leaving these 'features' enabled allows attackers (or hopefully just your pentester) on the same network to capture password hashes by responding to these queries with, "Yes, that server name is my IP address, but please authenticate to access me!"
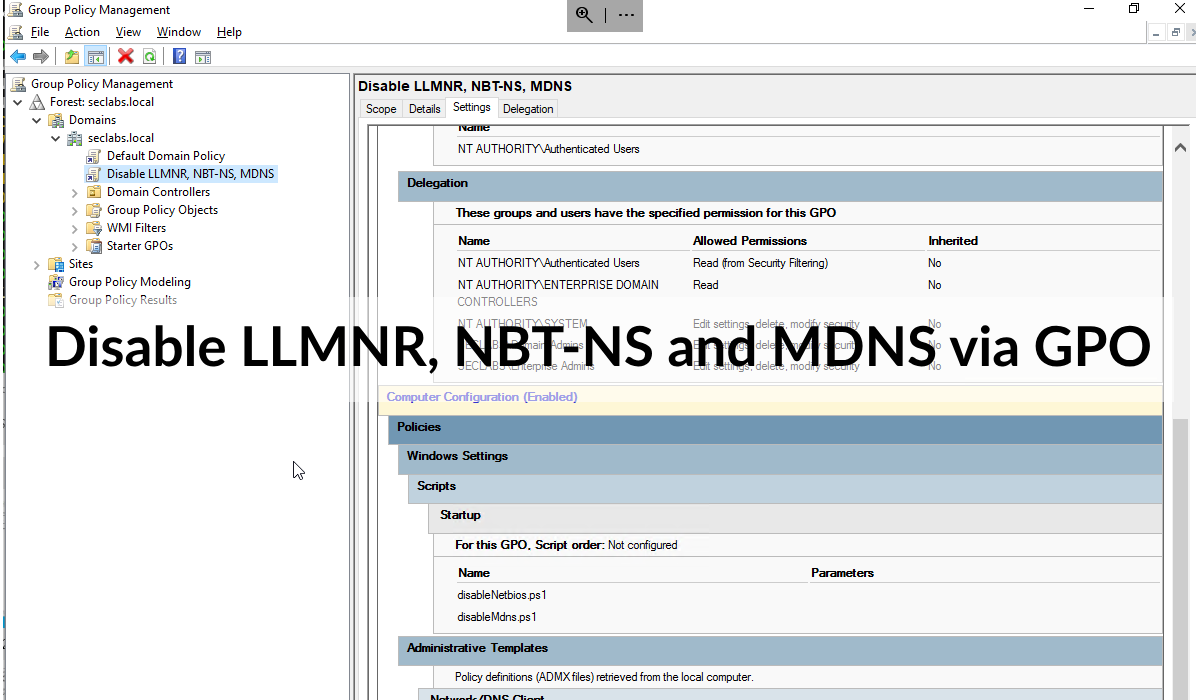
To disable these features, here's an exported GPO that you can import into your domain:

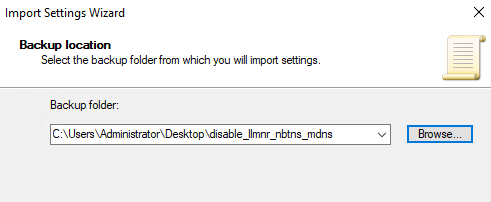
Extract the zip file on your server, create a new blank GPO and click Import Settings.
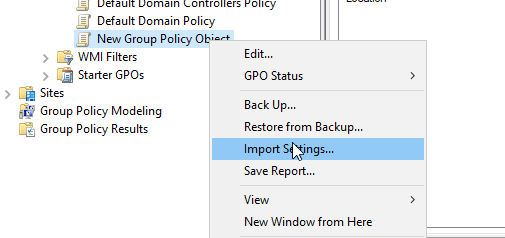
Selecting the downloaded GPO's folder should show a backed up GPO with the following settings:
- Setting to disable LLMNR.
- Settings to create registry keys to disable NBT-NS and MDNS.
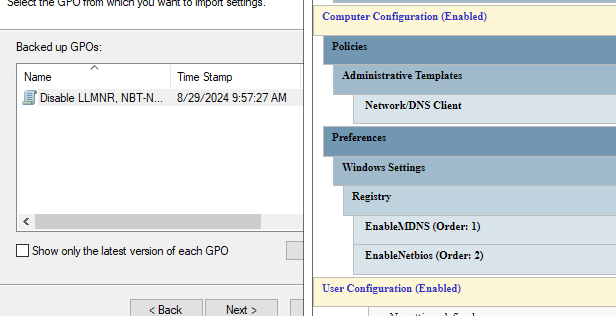
You can safely select "copy identically from source" and ignore the Warnings about security principals not being resolved as they don't exist in your domain.
After the import is complete, apply the GPO across your environment as you would with any other GPO.
Impact of Disabling These Protocols
- Disabling LLMNR and NBT-NS typically will not have any impact.
- If it does then you've got hosts relying on these protocols for name resolution!
- Disabling MDNS may have an impact - mostly for service/device discovery.
- Workstations may not be able to find wireless screen mirroring devices (e.g. Chromecasts, Printers and anything else that relies on MDNS).
- If this is a requirement ensure you test the MDNS registry key carefully!
- Workstations may not be able to find wireless screen mirroring devices (e.g. Chromecasts, Printers and anything else that relies on MDNS).
Side note: If you need to disable LLMNR, you probably also should look at Enabling and Requiring SMB Signing.
Creating Your Own GPO
Don't trust my zip file? You can recreate the GPO pretty easily.
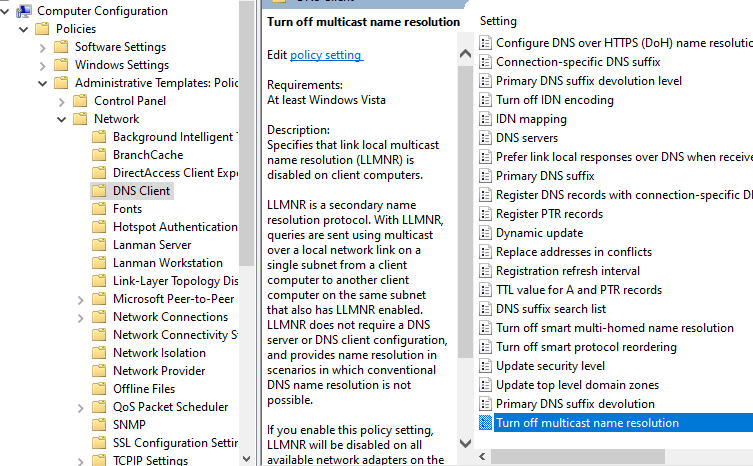
LLMNR
Computer Configuration -> Policies -> Administrative Templates -> Network -> DNS Client -> Turn off multicast name resolution (Enable)
NBT-NS
Option 1: Registry Key
There are two ways to disable NBT-NS. An ADMX template option exists on Insider builds, although there's reports that this doesn't work?
We can instead just set the registry key directly which I've confirmed works.
Browse to the Registry key section in the GPO and create a Registry Item.
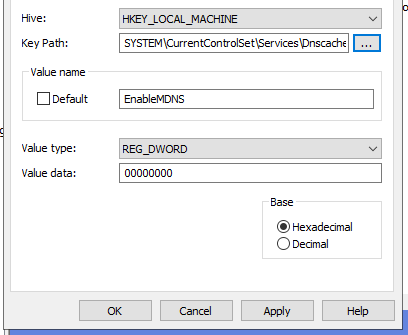
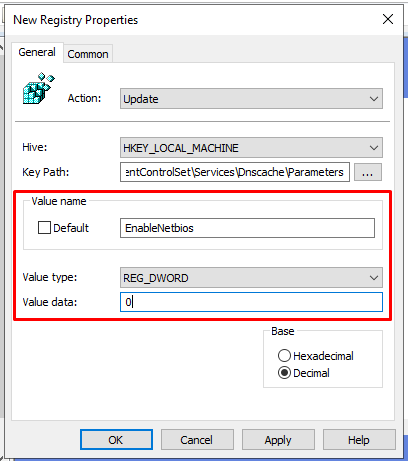
Target key: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Dnscache\Parameters
Create a REG_DWORD set to 0: EnableNetbios
Option 2: Startup Script (Not Preferred)
For older Windows clients (older than the blog post previously linked) that registry key does not do anything.
For this situation we can create a startup script that disables NBT-NS for each network interface.
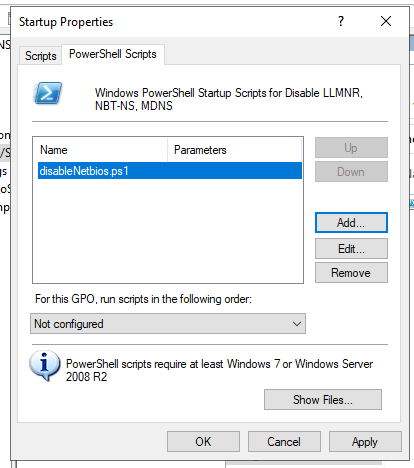
Create disableNetbios.ps1 with the following contents.
wmic nicconfig where "TcpipNetbiosOptions=0 or TcpipNetbiosOptions=1" call SetTcpipNetbios 2
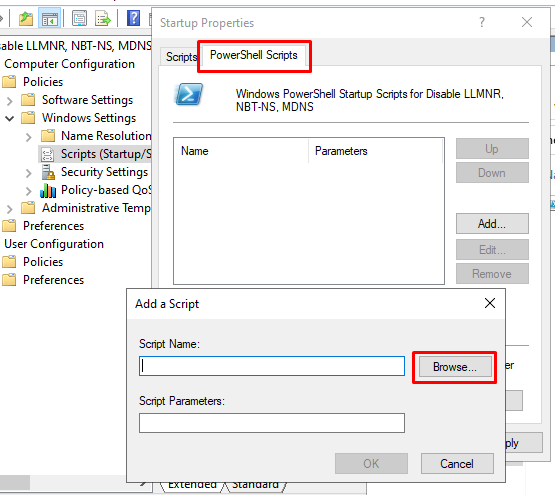
Computer Configuration -> Policies -> Windows Settings -> Scripts -> Startup (Properties) -> PowerShell Scripts -> Add
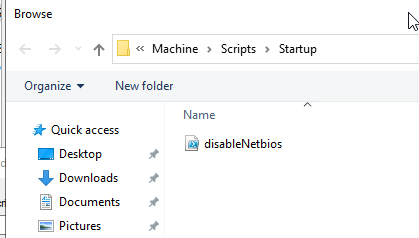
Startup scripts need to be placed in locations that are accessible to clients. For most environments, you'll probably be alright by placing it in the SYSVOL volume together with the GPO itself.
Click the Browse button and paste the startup script into the location that explorer opens in and accept all the prompts.
MDNS
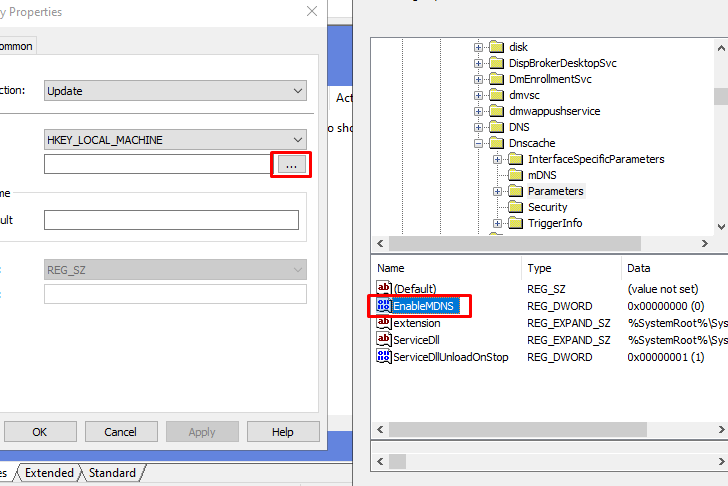
To Disable MDNS we just need to set a registry key.
Target key: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Dnscache\Parameters
Create a REG_DWORD set to 0: EnableMDNS