Bypassing Windows Login Without Password
Forgot your Windows password? Or maybe you're in physical possession of a device that you don't have the password for? Here's a trick to bypass that login screen.
This trick is a pretty old one that most pentesters know about, but it can still come in handy when physical acquisition of devices is on the table.
Or alternatively maybe your old uncle bob has inevitably forgotten their Windows password and they've asked you to fix it.
It's called the Sticky Keys hack.
Here's an overview of how it works and what we'll be doing:
- We use a USB drive to boot up a temporary operating system.
- We swap out the regular Sticky Keys program with the command prompt executable.
- Triggering Sticky Keys (press SHIFT 5 times) at the login screen now opens the command prompt with full access.
- Run some commands to reset your user's password.
- Login!
Image USB & Boot from Hirens
To start we'll need to prepare a USB drive from a seperate computer.
My goto tool for this is Ventoy.
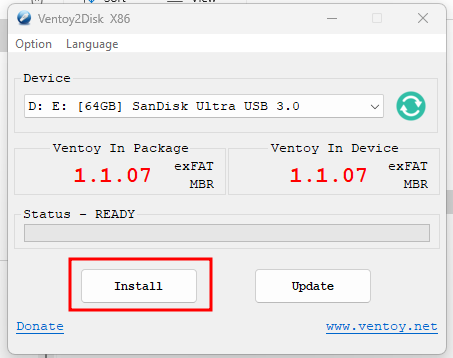
Once installed on the USB drive, you can simply drag ISOs to boot from into the USB drive that you wish to boot from and select them from a menu.
We'll be using Hiren's BootCD for this blog as it provides a Windows like environment which makes all of these steps trivial to follow.
Hiren's also publish their own guide for how to image it onto a USB if you prefer to use Rufus instead of Ventoy.
Once done, insert the USB drive into your target system and boot from it.
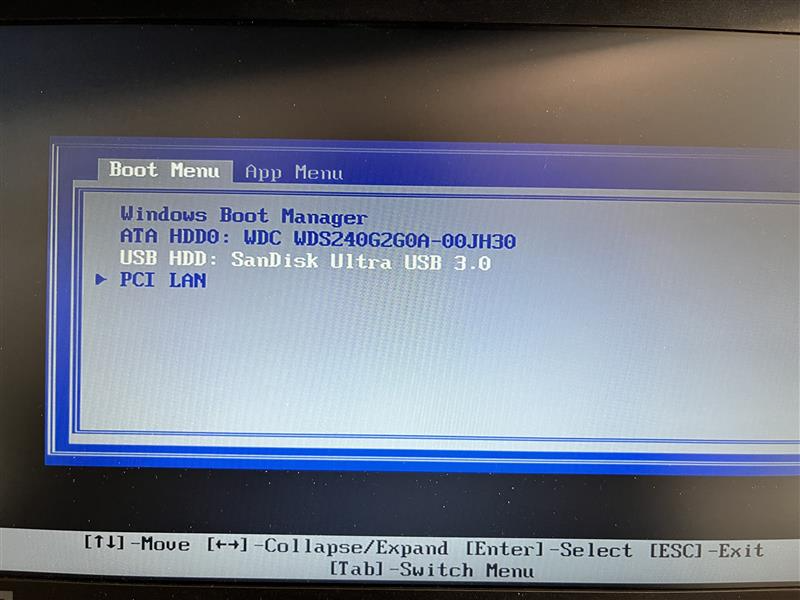
Sticky Keys Hack (Manual)
Once everything has booted we can open 'This PC' and locate the drive we want to modify (normally C:).
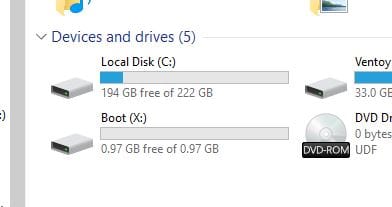
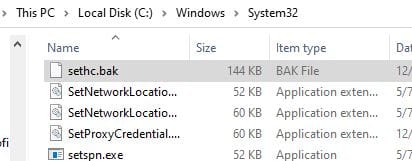
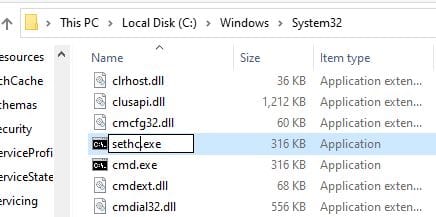
Backing Up sethc.exe
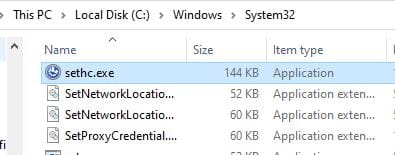
In the C:Windows\System32 directory you'll find the Sticky Keys utility that we want to replace.
We want to take a backup of the utility so we can restore it.
You can do this by simply renaming sethc.exe to sethc.bak.
Creating a Copy of cmd.exe
Now we can make a copy of cmd.exe and then rename it to sethc.exe .
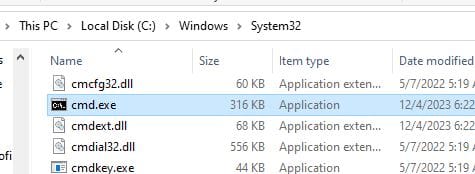
Changing Your Password
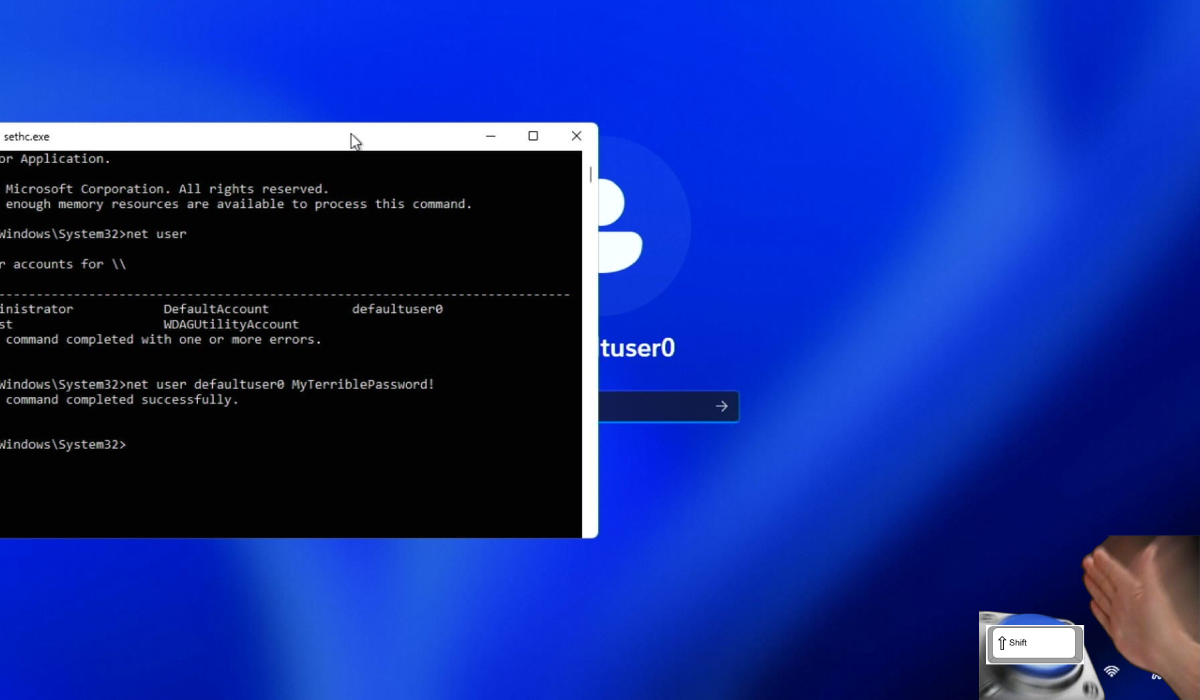
If you've followed along correctly, when you reboot and get back to the login screen, pressing SHIFT 5 times will now open up a command prompt window which runs with SYSTEM (highest) privileges.
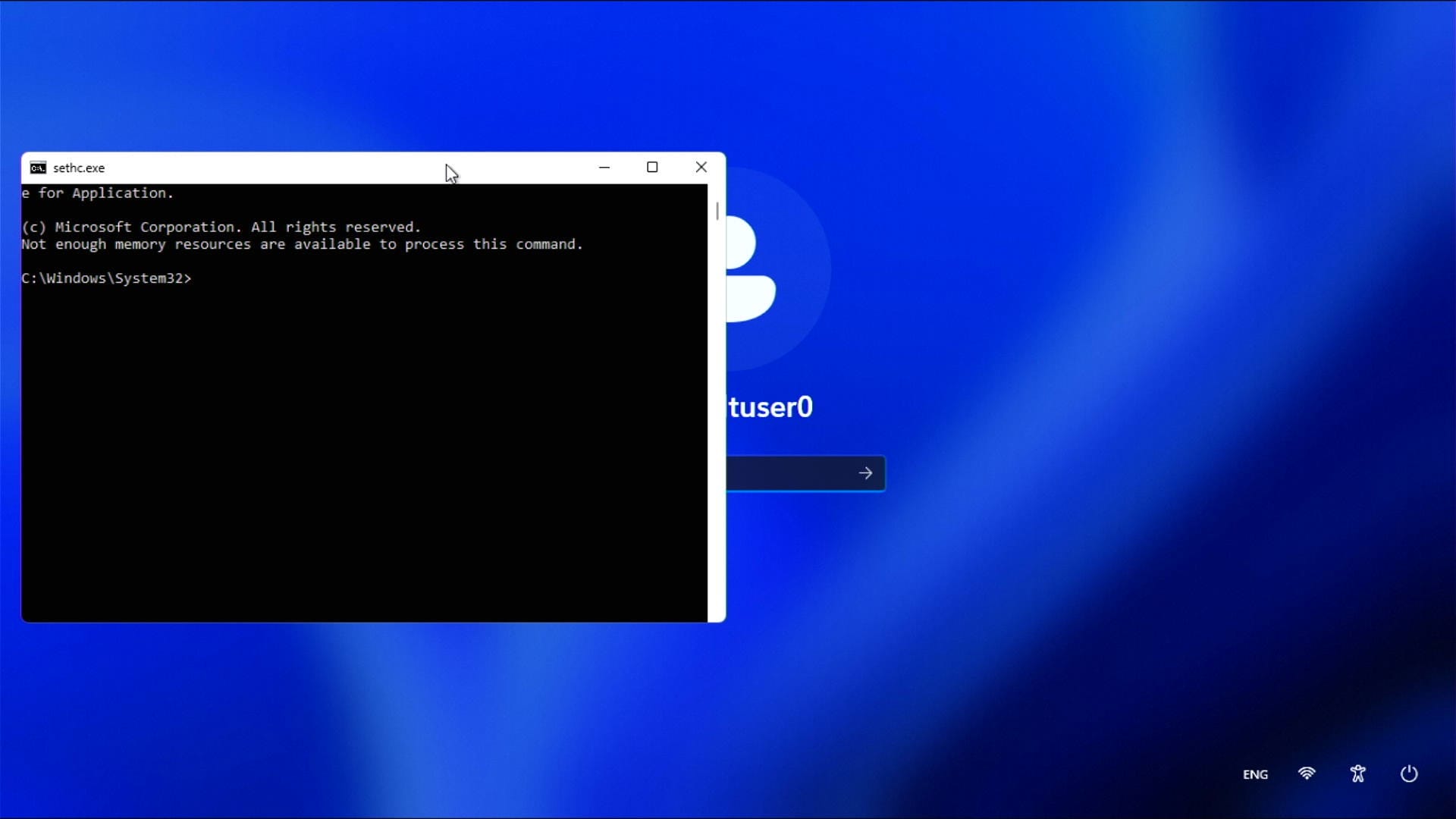
To list users on the system we can use the command net user.
To change the password for my account defaultuser0 we can type net user defaultuser0 MyTerriblePassword!.
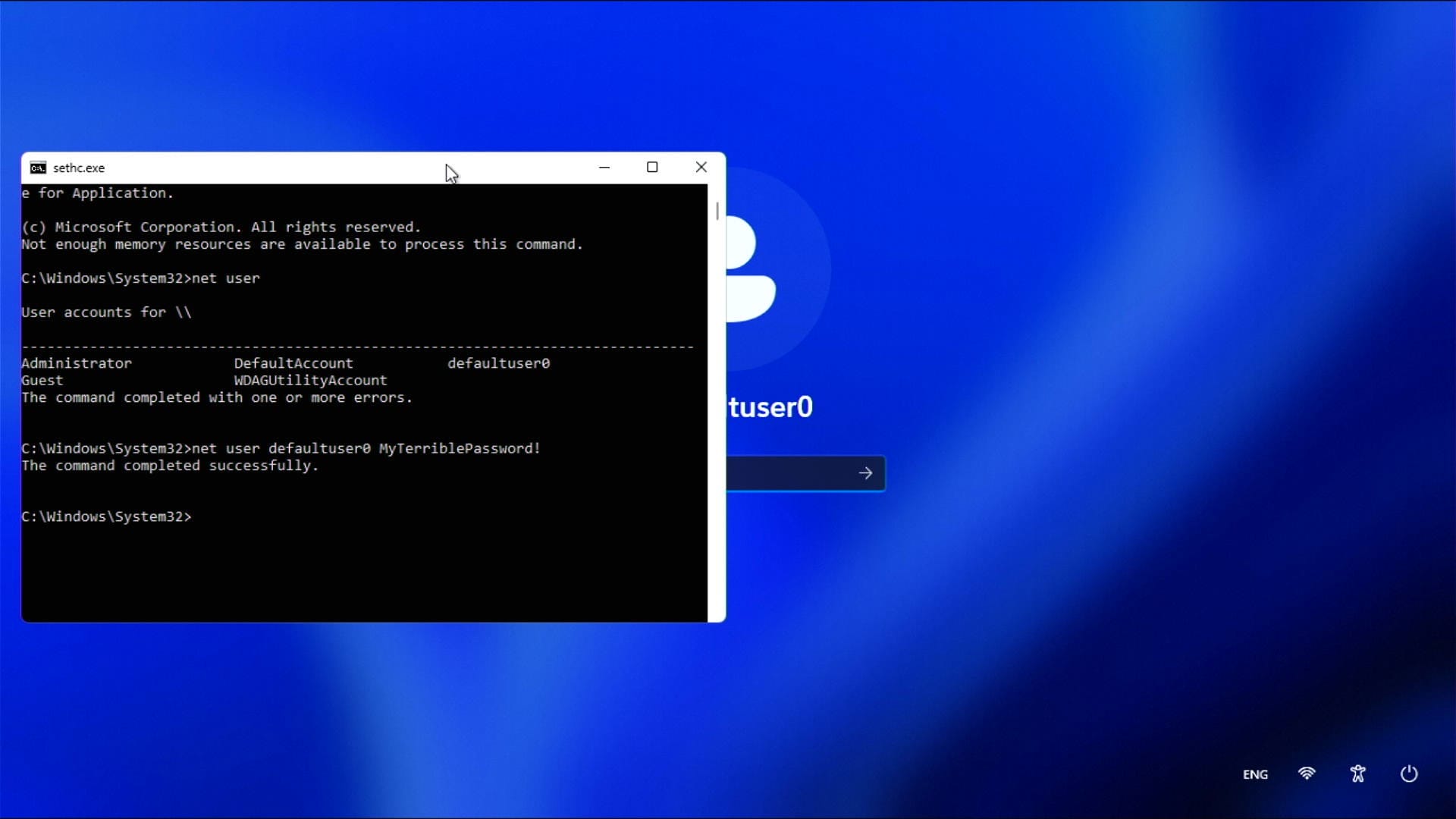
Hey presto we're in!
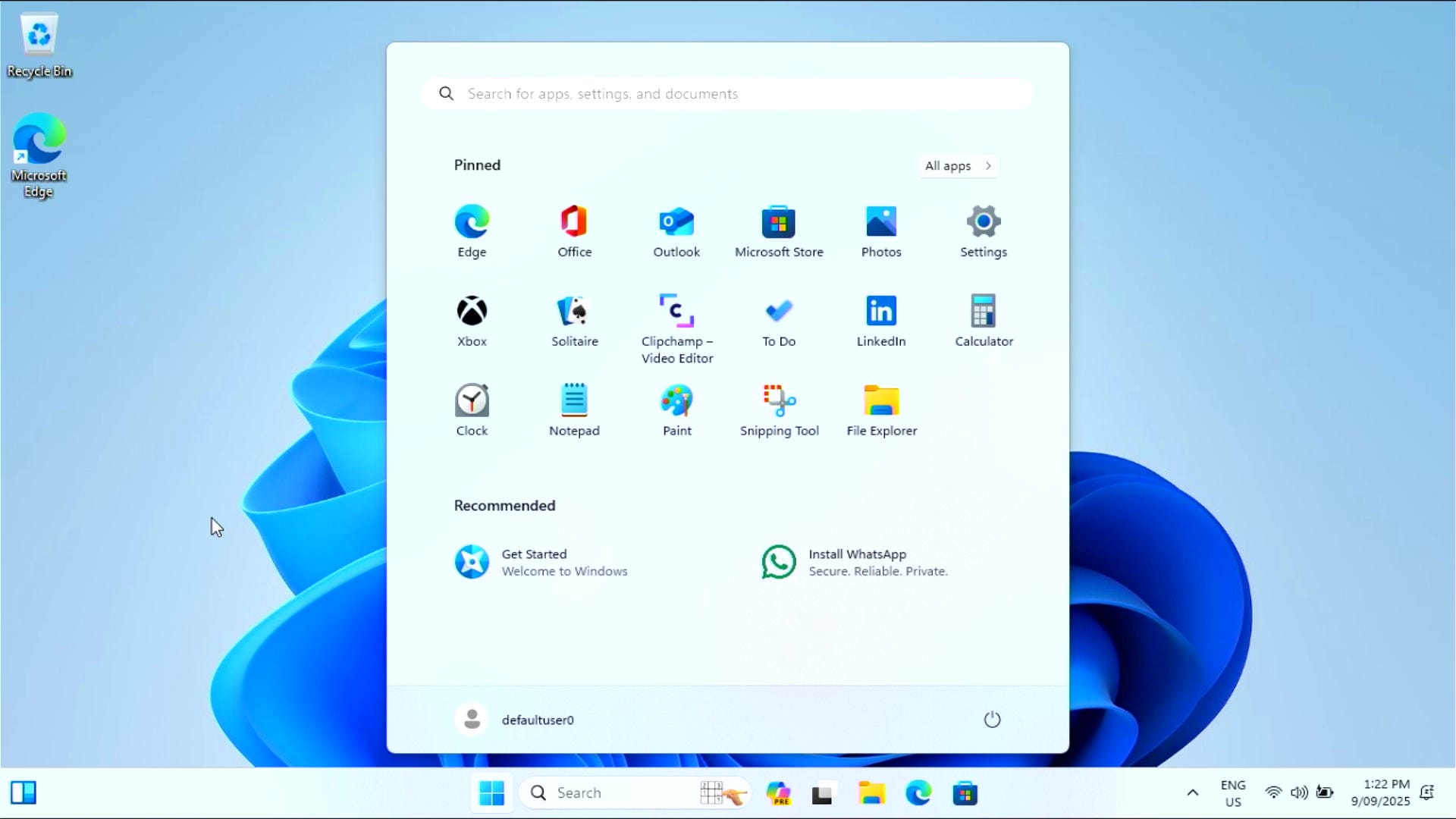
If instead of changing the password of an existing account you'd like to create a new account you can use the commands below to create a new account called bob and add them to the Administrators group.
net user bob MyTerriblePassword! /add
net localgroup Administrators bob /add
# Or maybe you want to be cheeky and make yourself an
# administrator when you weren't originally granted it ;)
net localgroup Administrators defaultuser0 /addNTPWEdit (GUI)
While the Sticky Keys hack can be performed from any live bootable OS there's also an easier option.
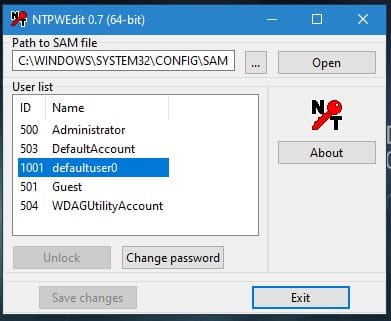
Hiren's Boot CD comes with NT Password Edit.
Launching this we can open the OS's SAM file (user password store) directly to view a list of users and change their passwords.
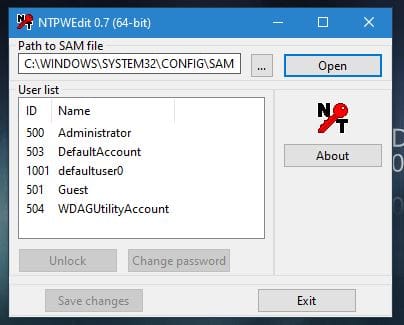
Changing an account's password is as simple as clicking the change password button.
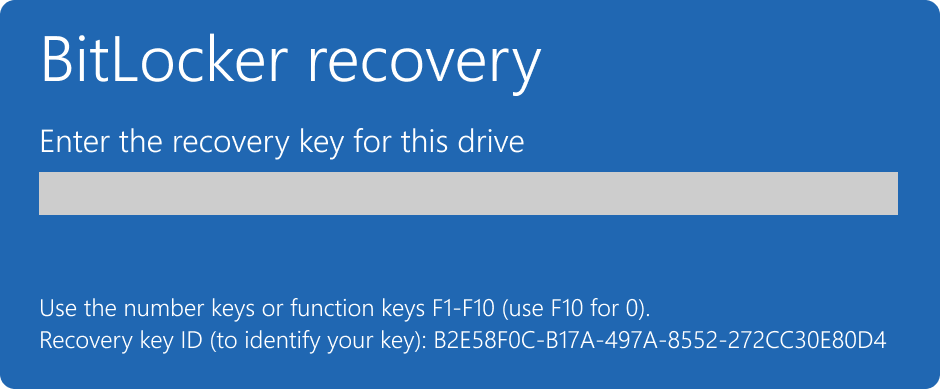
Bitlocker
All of the above assumes Bitlocker (disk encryption) isn't enabled.
If you have the recovery key you can just enter it in when prompted to unlock the drive and perform all of the above steps.
Fortunately, by default in corporate 365 environments, if the device is allocated to you, it's possible to retrieve your device's Bitlocker recovery key even if you're not an administrator.
Links below: https://aka.ms/aadrecoverykey